-
Notifications
You must be signed in to change notification settings - Fork 2
/
data-cc.sql
346 lines (339 loc) · 147 KB
/
data-cc.sql
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
CREATE EXTENSION IF NOT EXISTS "uuid-ossp";
DO $$
DECLARE
pl_id UUID := uuid_generate_v4();
p1 UUID := uuid_generate_v4();
p2 UUID := uuid_generate_v4();
p3 UUID := uuid_generate_v4();
p4 UUID := uuid_generate_v4();
p5 UUID := uuid_generate_v4();
p6 UUID := uuid_generate_v4();
p7 UUID := uuid_generate_v4();
p8 UUID := uuid_generate_v4();
p9 UUID := uuid_generate_v4();
p10 UUID := uuid_generate_v4();
p11 UUID := uuid_generate_v4();
p12 UUID := uuid_generate_v4();
p13 UUID := uuid_generate_v4();
p14 UUID := uuid_generate_v4();
p15 UUID := uuid_generate_v4();
p16 UUID := uuid_generate_v4();
p17 UUID := uuid_generate_v4();
p18 UUID := uuid_generate_v4();
p19 UUID := uuid_generate_v4();
p20 UUID := uuid_generate_v4();
p21 UUID := uuid_generate_v4();
p22 UUID := uuid_generate_v4();
p23 UUID := uuid_generate_v4();
p24 UUID := uuid_generate_v4();
p25 UUID := uuid_generate_v4();
p26 UUID := uuid_generate_v4();
p27 UUID := uuid_generate_v4();
p28 UUID := uuid_generate_v4();
p29 UUID := uuid_generate_v4();
p30 UUID := uuid_generate_v4();
p31 UUID := uuid_generate_v4();
p32 UUID := uuid_generate_v4();
p33 UUID := uuid_generate_v4();
p34 UUID := uuid_generate_v4();
p35 UUID := uuid_generate_v4();
p36 UUID := uuid_generate_v4();
p37 UUID := uuid_generate_v4();
p38 UUID := uuid_generate_v4();
p39 UUID := uuid_generate_v4();
p40 UUID := uuid_generate_v4();
p41 UUID := uuid_generate_v4();
p42 UUID := uuid_generate_v4();
p43 UUID := uuid_generate_v4();
p44 UUID := uuid_generate_v4();
p45 UUID := uuid_generate_v4();
p46 UUID := uuid_generate_v4();
p47 UUID := uuid_generate_v4();
p48 UUID := uuid_generate_v4();
p49 UUID := uuid_generate_v4();
p50 UUID := uuid_generate_v4();
p51 UUID := uuid_generate_v4();
p52 UUID := uuid_generate_v4();
p53 UUID := uuid_generate_v4();
p54 UUID := uuid_generate_v4();
p55 UUID := uuid_generate_v4();
p56 UUID := uuid_generate_v4();
p57 UUID := uuid_generate_v4();
p58 UUID := uuid_generate_v4();
p59 UUID := uuid_generate_v4();
p60 UUID := uuid_generate_v4();
p61 UUID := uuid_generate_v4();
p62 UUID := uuid_generate_v4();
p63 UUID := uuid_generate_v4();
p64 UUID := uuid_generate_v4();
p65 UUID := uuid_generate_v4();
p66 UUID := uuid_generate_v4();
p67 UUID := uuid_generate_v4();
p68 UUID := uuid_generate_v4();
p69 UUID := uuid_generate_v4();
p70 UUID := uuid_generate_v4();
p71 UUID := uuid_generate_v4();
p72 UUID := uuid_generate_v4();
p73 UUID := uuid_generate_v4();
p74 UUID := uuid_generate_v4();
BEGIN
INSERT INTO public.pattern_language (id, name, uri, graph, logo) VALUES (pl_id, 'Cloud Computing Patterns', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns', null, 'https://www.cloudcomputingpatterns.org/img/book.png');
INSERT INTO public.pattern_schema (pattern_language_id) VALUES (pl_id);
INSERT INTO public.pattern_section_schema (id, label, name, position, type, pattern_schema_pattern_language_id) VALUES (uuid_generate_v4(), 'Intend', 'Intend', 0, 'any', pl_id);
INSERT INTO public.pattern_section_schema (id, label, name, position, type, pattern_schema_pattern_language_id) VALUES (uuid_generate_v4(), 'Icon', 'Icon', 1, 'any', pl_id);
INSERT INTO public.pattern_section_schema (id, label, name, position, type, pattern_schema_pattern_language_id) VALUES (uuid_generate_v4(), 'Driving Question', 'Driving Question', 2, 'any', pl_id);
INSERT INTO public.pattern_section_schema (id, label, name, position, type, pattern_schema_pattern_language_id) VALUES (uuid_generate_v4(), 'Solution Sketch', 'Solution Sketch', 5, 'any', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p1, 'Infrastructure as a Service (IaaS)', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/infrastructureAsAService(iaas)', '{"Icon": "", "Intend": "Providers share physical and virtual hardware IT resources between customers to enable self-service, rapid elasticity, and pay-per-use pricing.", "Context": "In the scope of [Periodic Workloads](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FperiodicWorkload) with reoccurring peaks and the special case of [Once-in-a-lifetime Workloads](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252Fonce-in-a-lifetimeWorkload) with one dramatic increase in workload, IT resources have to be provisioned flexibly.", "Solution": "A provider offers physical and virtual hardware, such as servers, storage and networking infrastructure that can be provisioned and decommissioned quickly through a self-service interface.", "Solution Sketch": "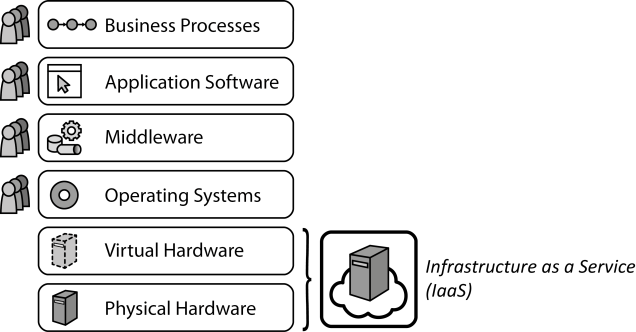", "Driving Question": "How can different customers share a physical hosting environment so that it can be used on-demand with a pay-per-use pricing model?"}', 'http://www.cloudcomputingpatterns.org/icons/infrastructure_as_a_service_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p2, 'Exactly-once Delivery', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/exactly-onceDelivery', '{"Icon": "", "Intend": "For many critical systems duplicate messages are inacceptable. The messaging system ensures that each message is delivered exactly once by filtering possible message duplicates automatically.", "Context": "Message duplicity is a very critical design issue for Distributed Applications and or application components that exchange messages via a Message-oriented Middleware.", "Solution": "Upon creation, each message is associated with a unique message identifier. This identifier is used to filter message duplicates during their traversal from sender to receiver.", "Solution Sketch": "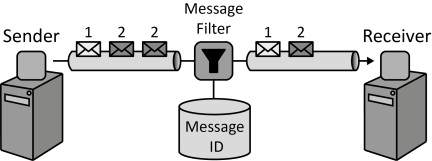", "Driving Question": "How can it be assured that a message is delivered only exactly once to a receiver?"}', 'http://www.cloudcomputingpatterns.org/icons/exactly_once_delivery_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p3, 'Execution Environment', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/executionEnvironment', '{"Icon": "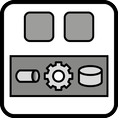", "Intend": "To avoid duplicate implementation of functionality, application components are deployed to a hosting environment providing middleware services as well as often used functionality.", "Context": "Applications often use similar functions, for example, to access networking interfaces, display user interfaces, access storage of the server etc. In this case, each application implements similar components that could be shared with other applications. Sharing such common functionality between applications would also result in a better utilization of the environment.", "Solution": "Common functionality is summarized in an Execution Environment providing functionality in platform libraries to be used in custom application implementations and in the form of the middleware. The environment, thus, executes custom application components and provides common functionality for data storages, communication etc.", "Solution Sketch": "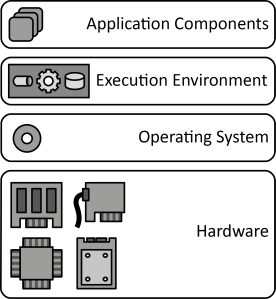", "Driving Question": "How can multiple application components share a hosting environment efficiently?"}', 'http://www.cloudcomputingpatterns.org/icons/execution_environment_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p4, 'At-least-once Delivery', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/at-least-onceDelivery', '{"Icon": "", "Intend": "In case of failures that lead to message loss or take too long to recover from, messages are retransmitted to assure they are delivered at least once.", "Context": "Sometimes, message duplicity can be coped with by the application using a Message-oriented Middleware. Therefore, for scenarios where message duplicates are uncritical, it shall still be ensured that messages are received.", "Solution": "For each message retrieved by a receiver an acknowledgement is sent back to the message sender. In case this acknowledgement is not received after a certain time frame, the message is resend.", "Solution Sketch": "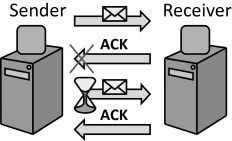", "Driving Question": "How can communication partners or a Message-oriented Middleware ensure that messages are received successfully?"}', 'http://www.cloudcomputingpatterns.org/icons/at_least_once_delivery_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p5, 'Transaction-based Delivery', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/transaction-basedDelivery', '{"Icon": "", "Intend": "Clients retrieve messages under a transactional context to ensure that messages are received by a handling component.", "Context": "While a Message-oriented Middleware can control traversing messages, it may be necessary to assure that messages are actually received successfully from a message queue by the client.", "Solution": "The Message-oriented Middleware and the client reading a message from a queue participate in a transaction. All operations involved in the reception of a message are, therefore, performed under one transactional context guaranteeing ACID behavior.", "Solution Sketch": "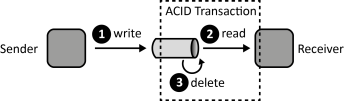", "Driving Question": "How can it be ensured that messages are only deleted from a message queue if they have been received successfully?"}', 'http://www.cloudcomputingpatterns.org/icons/transaction_based_delivery_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p6, 'Static Workload', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/staticWorkload', '{"Icon": "", "Intend": "IT resources with an equal utilization over time experience Static Workload.", "Context": "Static Workloads are characterized by a more-or-less flat utilization profile over time within certain boundaries.", "Solution": "An application experiencing Static Workload is less likely to benefit from an elastic cloud that offers a pay-per-use billing, because the number of required resources is constant.", "Solution Sketch": "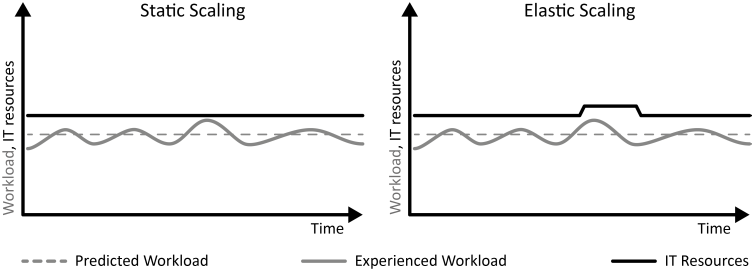", "Driving Question": "How can an equal utilization be characterized and how can applications experiencing this workload benefit from cloud computing?"}', 'http://www.cloudcomputingpatterns.org/icons/static_workload_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p7, 'Environment-based Availability', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/environment-basedAvailability', '{"Icon": "", "Intend": "A cloud provider guarantees the availability of the environment hosting individual nodes, such as virtual servers or hosted application components.", "Context": "A cloud provider offers an Elastic Infrastructure or an Elastic Platform on which customers may deploy application components. The availability of this environment has to be expressed so that customers may match their requirements.", "Solution": "The provider assures availability for the provided environment, thus, for the availability of the Elastic Platform or the Elastic Infrastructure as a whole, for example, the availability for at-least-once provisioned component or virtual server and the availability to provision replacements in case of failures is assured. There is no notion of availability for individual application components or virtual servers deployed in this environment.", "Solution Sketch": "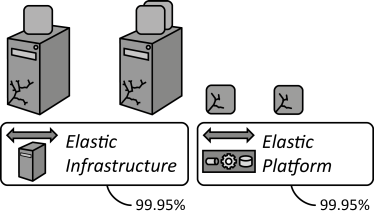", "Driving Question": "How can providers express availability in an environmental-centric fashion, so that customers may estimate the availability of hosted applications?"}', 'http://www.cloudcomputingpatterns.org/icons/environment_based_availability_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p8, 'Hypervisor', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hypervisor', '{"Icon": "", "Intend": "To enable the elasticity of clouds, the time required to provision and decommission servers is reduced through hardware virtualization.", "Context": "If multiple applications are deployed on a physical server they may have to consider the other applications in their configuration. For example, if applications require the same network ports, access the same directories in the local file system etc. This sharing of common underlying physical hardware between different applications shall be simplified while also reducing dependencies of the application on the physical server.", "Solution": "A Hypervisor abstracts the hardware of a shared physical server into virtualized hardware. On this virtual hardware, different operating systems and middleware are installed to host applications sharing the physical server while being isolated from each other regarding the use of physical hardware, such as central processing units (CPU), memory, disk storage, and networking.", "Solution Sketch": "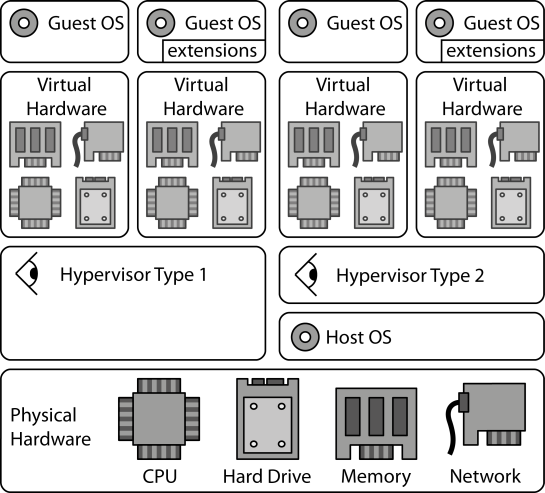", "Driving Question": "How can virtual hardware that has been abstracted from physical hardware be used in applications?"}', 'http://www.cloudcomputingpatterns.org/icons/hypervisor_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p9, 'Elastic Infrastructure', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticInfrastructure', '{"Icon": "", "Intend": "Hosting of virtual servers, disk storage, and configuration of network connectivity is offered via a self-service interface over a network.", "Context": "An application experiences Periodic Workload, Once-in-a-lifetime Workload, Unpredictable Workload, or Continuously Changing Workload, the number of IT resources, such as servers, should be adjusted dynamically. In scope of the IaaS service model, the applications’ runtime infrastructure, thus, must support dynamic provisioning and decommissioning of virtual servers, disk storage and network connectivity.", "Solution": "An Elastic Infrastructure provides preconfigured virtual server images, storage and network connectivity that may be provisioned by customers using a self-service interface. Monitoring information is provided to inform about resource utilization required for traceable billing and automation of management tasks.", "Solution Sketch": "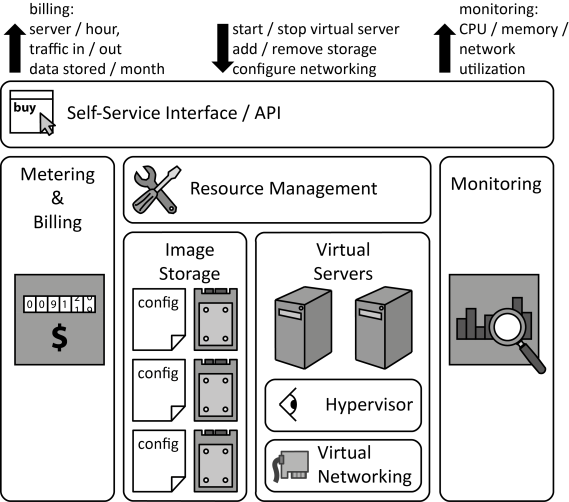", "Driving Question": "How do Cloud Offerings providing infrastructure resources behave and how should they be used in applications?"}', 'http://www.cloudcomputingpatterns.org/icons/elastic_infrastructure_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p10, 'Key-Value Storage', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/key-valueStorage', '{"Icon": "", "Intend": "Semi-structured or unstructured data is stored with limited querying support but high-performance, availability, and flexibility.", "Context": "To ensure availability and performance, a data storage offering shall be distributed among different IT resources and locations. Furthermore, changes of requirements or the fact that customers share a storage offering and have different requirements, raises the demand for a flexible data structure. as data structure validation during queries requires high-performance connectivity between distributed resources storing the data elements.", "Solution": "Pairs of identifiers (key) and associated data (value) are stored. No database schema or only a very limited one are supported to enforce a data structure. The expressiveness of queries is reduced significantly in favor of scalability and configurability: semi-structured on unstructured data can be scaled out among many IT resources without the need to access many of them for the evaluation of expressive queries.", "Solution Sketch": "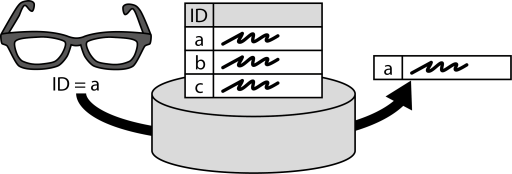", "Driving Question": "How can key-value elements be stored to support scale out and an adjustable data structure?"}', 'http://www.cloudcomputingpatterns.org/icons/key_value_storage_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p11, 'Hybrid Cloud', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridCloud', '{"Icon": "", "Intend": "Different clouds and static data centers are integrated to form a homogeneous hosting environment.", "Context": "A company is likely to use a large set of applications to support its business, which have versatile requirements making different Cloud Deployment Models suitable to host them.", "Solution": "[Private Clouds](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FprivateCloud), [Public Clouds](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FpublicCloud), [Community Clouds](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FcommunityCloud), and static data centers are integrated to deployed applications to the hosting environment best suited for their requirements while interconnection of these environments.", "Solution Sketch": "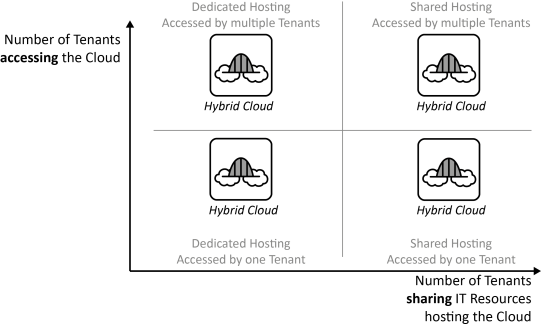", "Driving Question": "How can the cloud properties – on demand self-service, broad network access, pay-per-use, resource pooling, and rapid elasticity – be provided across clouds and other environments?"}', 'http://www.cloudcomputingpatterns.org/icons/hybrid_cloud_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p12, 'Relational Database', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/relationalDatabase', '{"Icon": "", "Intend": "Data is structured according to a schema that is enforced during data manipulation and enables expressive queries of handled data.", "Context": "Handled data is often comprised of large numbers of similar data elements. These data elements have certain dependencies among each other. If such structured data is queried, clients make certain assumptions about the data structure and the consistency of relations between the retrieved data elements.", "Solution": "Data elements are stored in tables where each column represents an attribute of a data element. Table columns may have dependencies in the way that entries in one table column must also be present in a corresponding column of a different table. These dependencies are enforced during data manipulations.", "Solution Sketch": "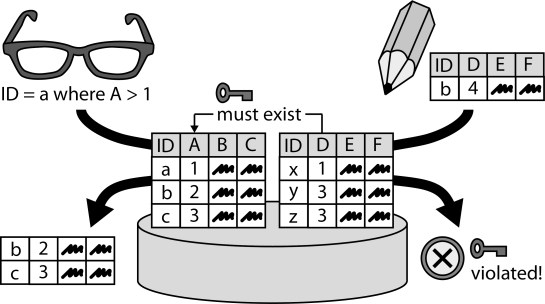", "Driving Question": "How can data elements be stored so that relations between them can be expressed and expressive queries are enabled to retrieve required information effectively?"}', 'http://www.cloudcomputingpatterns.org/icons/relational_database_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p13, 'Virtual Networking', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/virtualNetworking', '{"Icon": "", "Intend": "Networking resources are virtualized to empower customers to configure networks, firewalls, and remote access using a self-service interface.", "Context": "Application components deployed on Elastic Infrastructures and Elastic Platforms rely on physical network hardware to communicate with each other and the outside world. On this networking layer, different customers shall be isolated from each.", "Solution": "Physical networking resources, such as networking interface cards, switches, routers etc. are abstracted to virtualized ones. These Virtual Networking resources may share the same physical networking resources. Configuration is handled by customers through self-service interfaces.", "Solution Sketch": "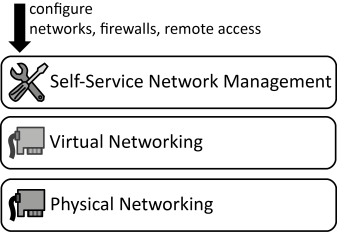", "Driving Question": "How can network connectivity between IT resources hosted in a cloud be configured dynamically and on-demand?"}', 'http://www.cloudcomputingpatterns.org/icons/virtual_networking_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p14, 'Blob Storage', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/blobStorage', '{"Icon": "", "Intend": "Data is provided in form of large files that are made available in a file system-like fashion by Storage Offerings that provides elasticity.", "Context": "Distributed cloud applications often need to handle large data elements, also referred to as binary large objects (blob). Examples are virtual server images managed in an Elastic Infrastructure, pictures, or videos.", "Solution": "Data elements are organized in a folder hierarchy similar to a local file system. Each data element is given a unique identifier comprised of its location in the folder hierarchy and a file name. This unique identifier is passed to the storage offerings to retrieve a file over a network.", "Solution Sketch": "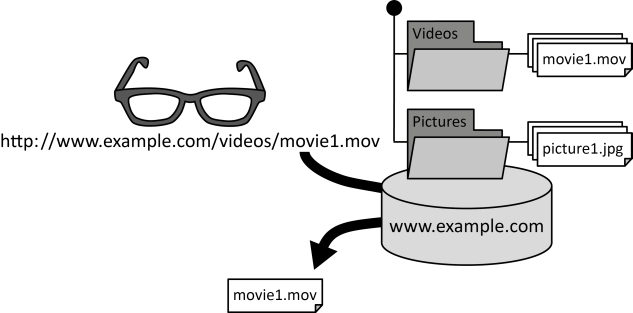", "Driving Question": "How can large files be stored, organized and made available over a network?"}', 'http://www.cloudcomputingpatterns.org/icons/blob_storage_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p15, 'Private Cloud', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/privateCloud', '{"Icon": "", "Intend": "IT resources are provided as a service exclusively to one customer in order to meet high requirements on privacy, security, and trust while enabling elastic use of a static resource pool as good as possible.", "Context": "Many factors, such as legal limitations, trust, and security regulations, motivate dedicated, company-internal hosting environments only accessible by employees and applications of a single company.", "Solution": "Cloud computing properties are enabled in a company-internal data center. Alternatively, the Private Cloud may be hosted exclusively in the data center of an external provider, then referred to as outsourced Private Cloud. Sometimes, [Public Cloud](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FpublicCloud) providers also offer means to create an isolated portion of their cloud made accessible to only one customer: a virtual Private Cloud.", "Solution Sketch": "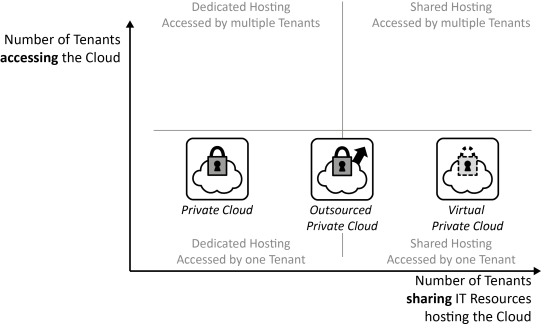", "Driving Question": "How can the cloud properties - on demand self-service, broad network access, pay-per-use, resource pooling, and rapid elasticity - be provided in environments with high privacy, security and trust requirements?"}', 'http://www.cloudcomputingpatterns.org/icons/private_cloud_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p16, 'Public Cloud', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/publicCloud', '{"Icon": "", "Intend": "IT resources are provided as a service to a very large customer group in order to enable elastic use of a static resource pool.", "Context": "A provider offering IT resources according to [IaaS](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FinfrastructureAsAService%28iaas%29), [PaaS](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FplatformAsAService%28paas%29), or [SaaS](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FsoftwareAsAService%28saas%29) has to maintain physical data centers. IT resources, nevertheless, shall be made accessible dynamically.", "Solution": "The hosting environment is shared between many customers possibly reducing the costs for an individual customer. Leveraging economies of scale enables a dynamic use of resources, because workload peaks of some customers occur during times of low workload of other customers.", "Solution Sketch": "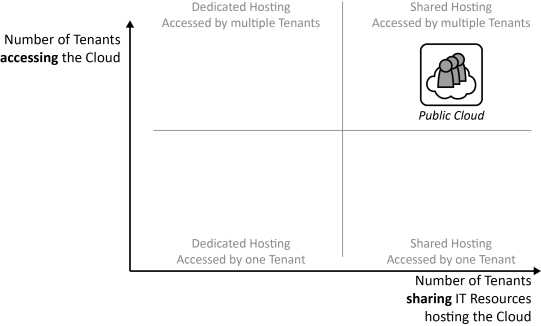", "Driving Question": "How can the cloud properties – on demand self-service, broad network access, pay-per-use, resource pooling, and rapid elasticity – be provided to a large customer group?"}', 'http://www.cloudcomputingpatterns.org/icons/public_cloud_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p17, 'Elastic Platform', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticPlatform', '{"Icon": "", "Intend": "Middleware for the execution of custom applications, their communication, and data storage is offered via a self-service interface over a network.", "Context": "One of the fundamental cloud properties is the sharing of resources among a large number of customers to leverage economy of scale. Extending resource sharing between customers to the operating systems and middleware increases the beneficial effects of economies of scale as the utilization of these resources can be increased.", "Solution": "Application components of different customers are hosted on shared middleware provided and maintained by the provider. Customers may deploy custom application components to this middleware using a self-service interface. This unification enables resource sharing and an automation of certain management tasks on the provider side, for example, provisioning of applications, update management.", "Solution Sketch": "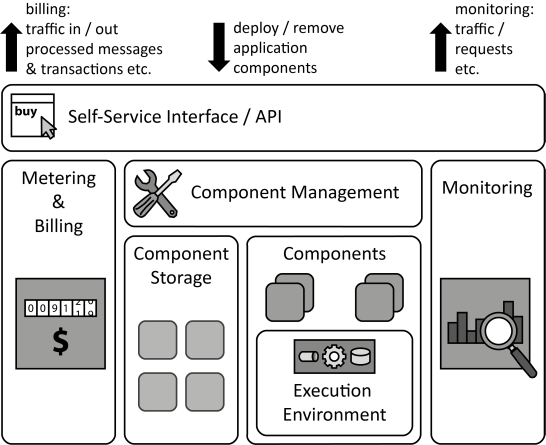", "Driving Question": "How do Cloud Offerings providing Execution Environments behave and how should they be used in applications?"}', 'http://www.cloudcomputingpatterns.org/icons/elastic_platform_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p18, 'Periodic Workload', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/periodicWorkload', '{"Icon": "", "Intend": "IT resources with a peaking utilization at reoccurring time intervals experience periodic workload.", "Context": "In our real lives, periodic tasks and routines are very common. For example, monthly paychecks, monthly telephone bills, yearly car checkups, weekly status reports, or the daily use of public transport during rush hour, all these tasks and routines occur in well-defined intervals.", "Solution": "From a customer perspective the cost-saving potential in scope of Periodic Workload is to use a provider with a pay-per-use pricing model allowing the decommissioning of resources during non-peak times.", "Solution Sketch": "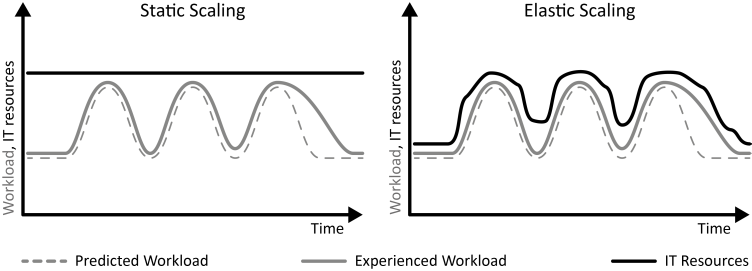", "Driving Question": "How can a periodically peaking utilization over time be characterized and how can applications experiencing this workload benefit from cloud computing?"}', 'http://www.cloudcomputingpatterns.org/icons/periodic_workload_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p19, 'Once-in-a-lifetime Workload', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/once-in-a-lifetimeWorkload', '{"Icon": "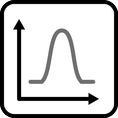", "Intend": "IT resources with an equal utilization over time disturbed by a strong peak occurring only once experience Once-in-a-lifetime Workload.", "Context": "As a special case of [Periodic Workload](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FperiodicWorkload), the peaks of periodic utilization can occur only once in a very long timeframe. Often, this peak is known in advance as it correlates to a certain event or task.", "Solution": "The elasticity of a cloud is used to obtain IT resources necessary. The provisioning and decommissioning of IT resources can often be realized as a manual task, because it is performed at a known point in time.", "Solution Sketch": "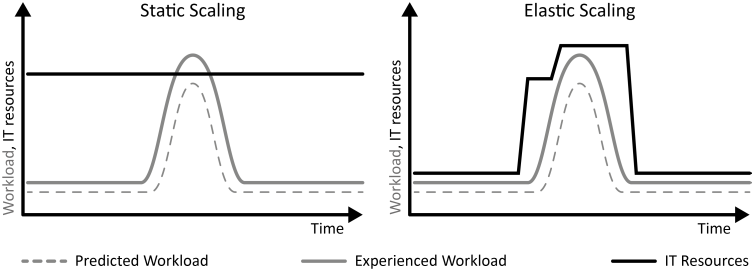", "Driving Question": "How can equal utilization with a one-time peak be characterized and how can applications experiencing this workload benefit from cloud computing?"}', 'http://www.cloudcomputingpatterns.org/icons/once_in_a_lifetime_workload_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p20, 'Map Reduce', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/mapReduce', '{"Icon": "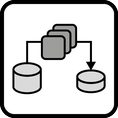", "Intend": "Large data sets to be processed are divided into smaller data chunks and distributed among processing application components. Individual results are later consolidated.", "Context": "Cloud applications often have to handle very large amounts of data, which have to be processed efficiently. As Distributed Applications are designed to scale out, data processing should be distributed among multiple application component instances in a similar means. Afterwards, results of these distributed components have to be consolidated.", "Solution": "A large data set to be processed is split up and mapped to multiple application components handling data processing. Data Processing Components simultaneously execute the query to be performed on the assigned data chunks. Afterwards, the individual results of all Processing Components are consolidated or reduced into one result data set. During this reduction, additional functions, such calculations of sums, average values etc. may be used.", "Solution Sketch": "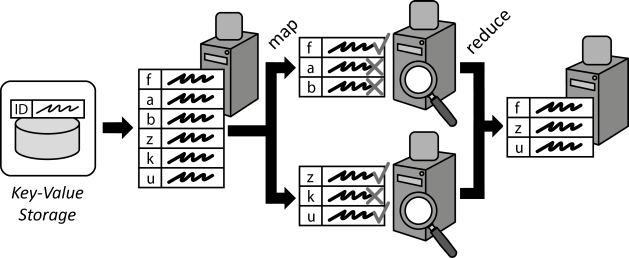", "Driving Question": "How can the performance of complex processing of large data sets be increased through scaling out?"}', 'http://www.cloudcomputingpatterns.org/icons/map_reduce_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p21, 'Platform as a Service (PaaS)', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/platformAsAService(paas)', '{"Icon": "", "Intend": "Providers share IT resources providing an application hosting environment between customers to enable self-service, rapid elasticity, and pay-per-use pricing.", "Context": "If many customers require similar hosting environments for their applications, there are many redundant installations resulting in an inefficient use of the overall cloud.", "Solution": "A cloud provider offers managed operating systems and middleware. Management operations are handled by the provider, such as the elastic scaling and failure resiliency of hosted applications.", "Solution Sketch": "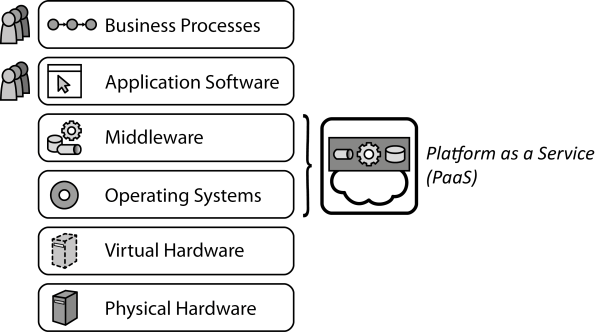", "Driving Question": "How can custom applications of the same customer or different customers share an execution environment so that it can be used on-demand with a pay-per-use pricing model?"}', 'http://www.cloudcomputingpatterns.org/icons/platform_as_a_service_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p22, 'Eventual Consistency', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/eventualConsistency', '{"Icon": "", "Intend": "If data is stored at different locations (replicas) to improve response time and avoid data loss in case of failures. Performance and the availability of data in case of network partitioning are enabled by ensuring data consistency eventually and not at all times.", "Context": "Using multiple replicas of data is vital to ensure resiliency of a storage offering towards resource failures. Keeping all these replicas in a consistent state, however, requires a significant overhead as multiple or all data replicas have to be accessed during read and write operations.", "Solution": "The consistency of data is relaxed. This reduces the number of replicas that have to be accessed during read and write operations. Data alterations are eventually transferred to all replicas by propagating them asynchronously over the connection network.", "Solution Sketch": "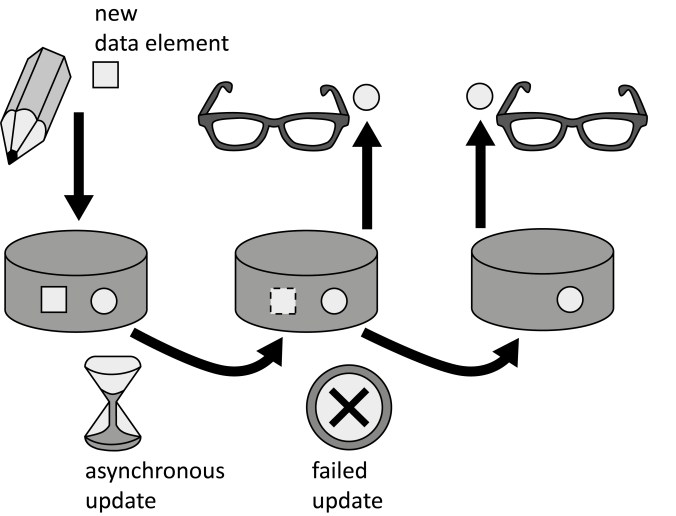", "Driving Question": "How can data be distributed among replicas with focus on increased availability and performance, while being resilient towards connectivity problems?"}', 'http://www.cloudcomputingpatterns.org/icons/eventual_consistency_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p23, 'Community Cloud', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/communityCloud', '{"Icon": "", "Intend": "IT resources are provided as a service to a group of customers trusting each other in order to enable collaborative elastic use of a static resource pool.", "Context": "Whenever companies collaborate, they commonly have to access shared applications and data to do business. While these companies trust each other due to established contracts etc., the handled data and application functionality may be very sensitive and critical to their business.", "Solution": "IT resources required by all collaborating partners are offered in a controlled environment accessible only by the community of companies that generally trust each other.", "Solution Sketch": "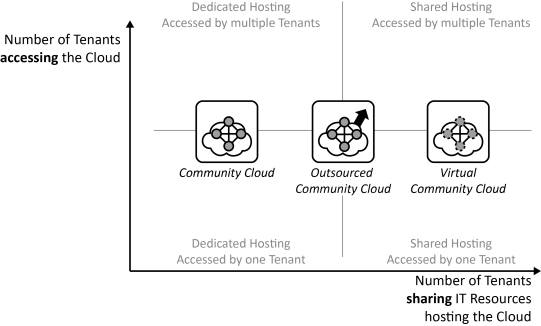", "Driving Question": "How can the cloud properties – on demand self-service, broad network access, pay-per-use, resource pooling, and rapid elasticity – be provided to exclusively to a group of customers forming a community of trust?"}', 'http://www.cloudcomputingpatterns.org/icons/community_cloud_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p24, 'Node-based Availability', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/node-basedAvailability', '{"Icon": "", "Intend": "A cloud provider guarantees the availability of individual nodes, such as individual virtual servers, middleware components or hosted application components.", "Context": "A provider offers an Elastic Infrastructure or an Elastic Platform and needs a means to express the availability for the offerings from which the customer may then compute the availability of the hosted application. First, conditions are defined that have to be fulfilled by an available offering. Second, the timeframe needs to be expressed for which the provider assures this availability.", "Solution": "The provider assures availability for each hosted application component, which is defined to be available if it is reachable and performs its function as advertised, i.e., it provides correct results. This timeframe is often expressed as a percentage. An availability of 99.95%, thus, means that a hosted component will be available during 99.95% of the time it is hosted at the provider.", "Solution Sketch": "", "Driving Question": "How can providers express availability in a node-centric fashion, so that customers may estimate the availability of hosted applications?"}', 'http://www.cloudcomputingpatterns.org/icons/node_based_availability_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p25, 'Timeout-based Delivery', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/timeout-basedDelivery', '{"Icon": "", "Intend": "Clients acknowledge message receptions to ensure that messages are received properly.", "Context": "In addition to ensuring that messages are not lost while they are traversing a Message-oriented Middleware it may, thus, also be required to assure that they are actually received by a client before they are deleted from a message queue.", "Solution": "To assure that a message is properly received, it is not deleted immediately after it has been read by a client, but is only marked as being invisible. In this state a message may not be read by another client. After a client has successfully read a message, it sends an acknowledgement to the message queue upon which reception the message is deleted.", "Solution Sketch": "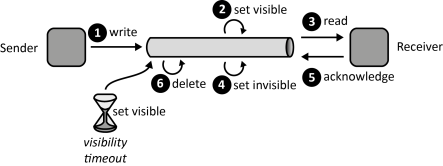", "Driving Question": "How can it be ensured that messages are only deleted from a message queue if they have been received successfully at least once?"}', 'http://www.cloudcomputingpatterns.org/icons/timeout_based_delivery_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p26, 'Block Storage', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/blockStorage', '{"Icon": "", "Intend": "Centralized storage is integrated into servers as a local hard drive managed by the operating system to enable access to this storage via the local file system.", "Context": "Virtual and non-virtualized servers offered as Infrastructure as a Service (IaaS) can be managed significantly easier if they do not store any state information locally, i.e., on their (virtual) hard drives. This eases their provisioning, decommissioning, and failure handling.", "Solution": "Centralized storage is accessed by servers as if it was a local hard drive, also referred to as block device.", "Solution Sketch": "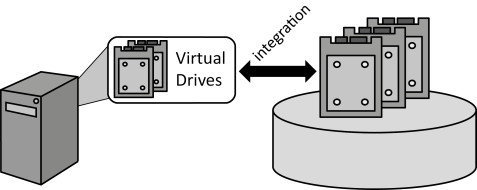", "Driving Question": "How can central storage be accessed as a local drive by servers and hosted applications?"}', 'http://www.cloudcomputingpatterns.org/icons/block_storage_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p27, 'Software as a Service (SaaS)', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/softwareAsAService(saas)', '{"Icon": "", "Intend": "Providers share IT resources providing human-usable application software between customers to enable self-service, rapid elasticity, and pay-per-use pricing.", "Context": "Small and medium enterprises may not have the manpower and know-how to develop custom software applications. Other applications have become commodity and are used by many companies, for example, office suites, collaboration software, or communications software.", "Solution": "A provider offers a complete software application to customers who may use it on-demand via a self-service interface.", "Solution Sketch": "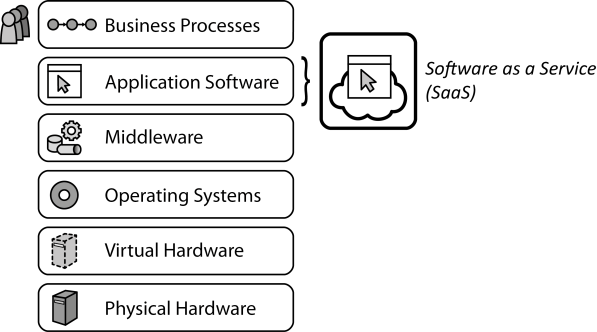", "Driving Question": "How can customers share a provider-supplied software application so that it can be used on-demand with a pay-per-use pricing model?"}', 'http://www.cloudcomputingpatterns.org/icons/software_as_a_service_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p28, 'Strict Consistency', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/strictConsistency', '{"Icon": "", "Intend": "Data is stored at different locations (replicas) to improve response time and to avoid data loss in case of failures while consistency of replicas is ensured at all times.", "Context": "To ensure failure tolerance, a storage offering duplicates data among multiple replicas. These replicas store the same set of data, so in case any of these replicas is lost, data may still be obtained and recovered from the other replicas.", "Solution": "Data is duplicated among several replicas to increase availability. A subset of data replicas is accessed by read and write operations. The ratio of the number of replicas accessed during read (r) and write (w) operations guarantees consistency: n < r + w", "Solution Sketch": "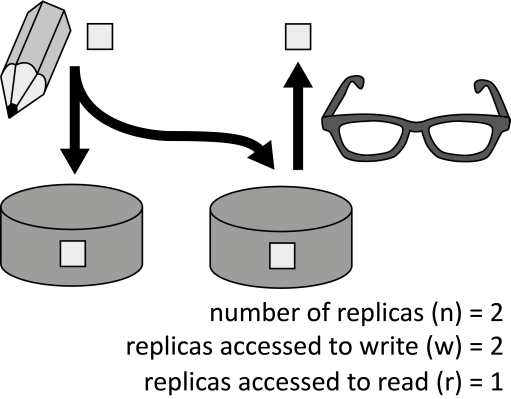", "Driving Question": "How can data be distributed among replicas to increase availability, while ensuring data consistency at all times?"}', 'http://www.cloudcomputingpatterns.org/icons/strict_consistency_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p29, 'Unpredictable Workload', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/unpredictableWorkload', '{"Icon": "", "Intend": "IT resources with a random and unforeseeable utilization over time experience unpredictable workload.", "Context": "Random workloads are a generalization of [Periodic Workloads](/patternlanguages/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns/https%25253A%25252F%25252Fpatternpedia.org%25252FpatternLanguages%25252FcloudComputingPatterns%25252FperiodicWorkload) as they require elasticity but are not predictable. Such workloads occur quite often in the real world.", "Solution": "Unplanned provisioning and decommissioning of IT resources is required. The necessary provisioning and decommissioning of IT resources is, therefore, automated to align the resource numbers to changing workload.", "Solution Sketch": "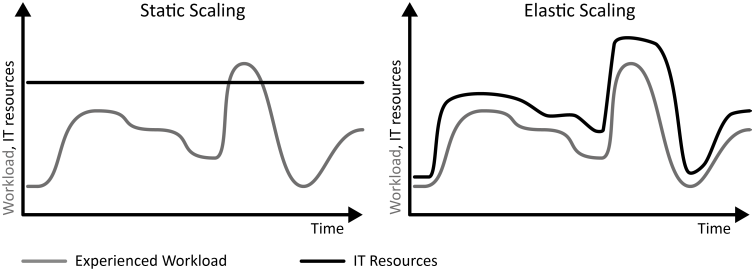", "Driving Question": "How can random and unforeseeable utilization be characterized and how can applications experiencing this workload benefit from cloud computing?"}', 'https://www.cloudcomputingpatterns.org/icons/unpredictable_workload_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p30, 'Message-oriented Middleware', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/message-orientedMiddleware', '{"Icon": "", "Intend": "Asynchronous message-based communication is provided while hiding complexity resulting from addressing, routing, or data formats from communication partners to make interaction robust and flexible.", "Context": "The application components of a Distributed Application are hosted on multiple cloud resources and have to exchange information with each other. Often, the integration with other cloud applications and non-cloud applications is also required.", "Solution": "Communication partners exchange information asynchronously using messages. The message-oriented middleware handles the complexity of addressing, availability of communication partners and message format transformation.", "Solution Sketch": "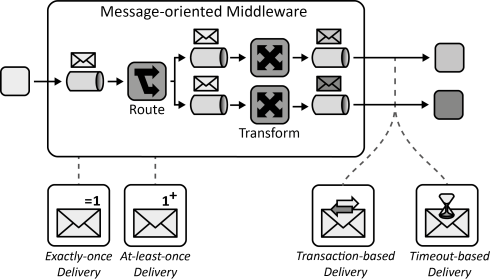", "Driving Question": "How can communication partners exchange information asynchronously with a communication partner?"}', 'http://www.cloudcomputingpatterns.org/icons/message_oriented_middleware_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p31, 'Continuously Changing Workload', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/continuouslyChangingWorkload', '{"Icon": "", "Intend": "IT resources with a utilization that grows or shrinks constantly over time experience Continuously Changing Workload.", "Context": "Many applications experience a long term change in workload.", "Solution": "Continuously Changing Workload is characterized by an ongoing continuous growth or decline of the utilization. Elasticity of clouds enables applications experiencing Continuously Changing Workload to provision or decommission resources with the same rate as the workload changes.", "Solution Sketch": "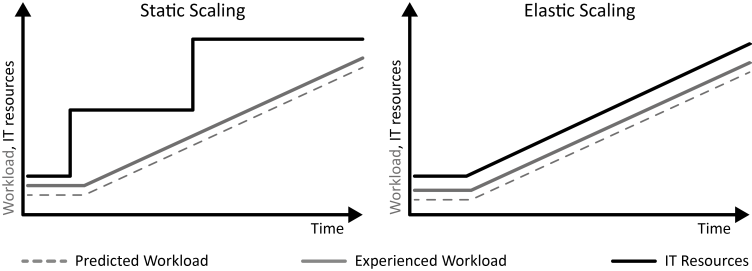", "Driving Question": "How can a continuous growth or decline in utilization be characterized and how can applications experiencing this workload benefit from cloud computing?"}', 'http://www.cloudcomputingpatterns.org/icons/continuously_changing_workload_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p32, 'Loose Coupling', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/looseCoupling', '{"Icon": "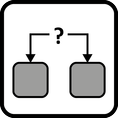", "Intend": "A communication intermediary separates application functionality from concerns of communication partners regarding their location, implementation platform, the time of communication, and the used data format.", "Context": "Information exchange between applications and their individual components as well as associated management tasks, such as scaling, failure handling, or update management can be simplified significantly if application components can be treated individually and the dependencies among them are kept to a minimum.", "Solution": "Communicating components and multiple integrated applications are decoupled from each other by interacting through a broker. This broker encapsulates the assumptions that communication partners would otherwise have to make about one other and, thus, ensures separation of concerns.", "Solution Sketch": "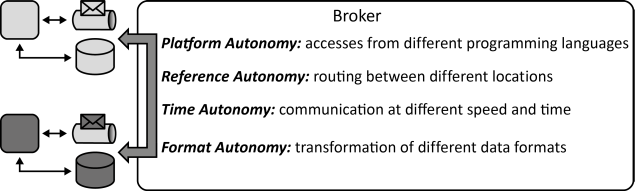", "Driving Question": "How can dependencies between Distributed Applications and between individual components of these applications be reduced?"}', 'https://www.cloudcomputingpatterns.org/icons/loose_coupling_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p33, 'Distributed Application', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/distributedApplication', '{"Icon": "Enter your input for this section here.", "Intend": "A cloud application divides provided functionality among multiple application components that can be scaled out independently.", "Context": "Applications have to respect the distribution and the scaling-out support of cloud environments in their architecture to efficiently benefit from it. Cloud applications, therefore, should to rely on multiple, possibly redundant IT resources. This can especially be the case if the cloud provider assures Environment-based Availability – the availability of the complete environment and not of single IT resources hosted in it.", "Solution": "The functionality of the application is divided into multiple independent components that provide a certain function. This componentization of application functionality introduces a logical decomposition of the application. These logical components are subsumed to multiple tiers to denote that they shall be deployed together physically, i.e., on one server (cluster).\n\n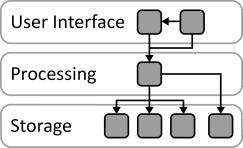\n\nLayer-based decomposition divides the application into separate logical layers. Components are restricted to access components of the same layer or one layer below.\n\n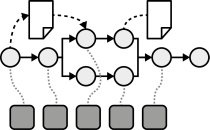\n\nProcess-based decomposition focuses on the business processes supported by the application. These processes are comprised out of activities that are executed in a specific order. Functionality is divided into components with respect to the supported business activity.\n\n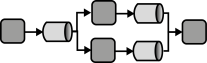\n\nPipes-and-filters-based decomposition focuses on for data-centric processing of an application. Each filter provides a certain function that is performed on input data and produces output data after processing. Multiple filters are interconnected with pipes, i.e, through messaging.", "Solution Sketch": "", "Driving Question": "How can application functionality be decomposed to be handled by separate application components?"}', 'https://www.cloudcomputingpatterns.org/icons/distributed_application_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p34, 'Stateful Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/statefulComponent', '{"Icon": "", "Intend": "Multiple instances of a scaled-out application component synchronize their internal state to provide a unified behavior.", "Context": "To benefit from a distributed cloud runtime environment, components of a Distributed Application are deployed to multiple cloud resources and their instances are scaled-out. Some of these application components may need to maintain an internal state, thus, the challenge arises that individual instances of application components should contain the same internal state, so that they present a unified behavior.", "Solution": "The internal state maintained by application component instances is replicated among all instances. Only small portions of shared information are used, for example, a configuration file stored centrally or configurations send by clients with every request.", "Solution Sketch": "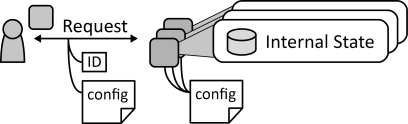", "Driving Question": "How can applications components that are scaled-out maintain a synchronized internal state?"}', 'https://www.cloudcomputingpatterns.org/icons/stateful_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p35, 'Stateless Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/statelessComponent', '{"Icon": "", "Intend": "State is handled external of application components to ease their scaling-out and to make the application more tolerant to component failures.", "Context": "The components of a Distributed Application are deployed among multiple cloud resources to benefit from this distributed runtime environment through scaling out.The most significant factor complicating addition and removal of component instances in this scope is the internal state maintained by them. In case of failure, this information may even be lost.", "Solution": "Application components are implemented in a fashion that they do not have an internal state. Instead, their state and configuration is stored externally in Storage Offerings or provided to the component with each request.", "Solution Sketch": "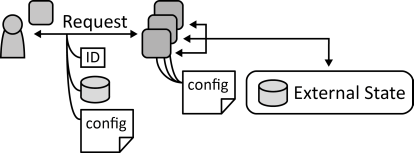", "Driving Question": "How can elasticity and robustness of an application component be increased?"}', 'https://www.cloudcomputingpatterns.org/icons/stateless_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p36, 'User Interface Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/userInterfaceComponent', '{"Icon": "", "Intend": "Interactive synchronous access to applications is provided to humans, while application-internal interaction is realized asynchronously when possible to ensure Loose Coupling. Furthermore, the user interface should be customizable to be used by different customers.", "Context": "User Interface Component instances part of a Distributed Application have to be added and removed easily from the application without affecting the user experience. The dependencies on other application components should, therefore, be reduced as much as possible.", "Solution": "The User Interface Component serves as a bridge between the synchronous access of the human user and the asynchronous communication used with other application components. State information held externally, as described by the Stateless Component pattern. It is, therefore, attached to requests, may be held in a part of the user interface that is deployed on the user’s access device, or may be obtained from external storage. Instances of User Interface Components are scaled based on the number of synchronous requests to is as described by the Elastic Load Balancer pattern.", "Solution Sketch": "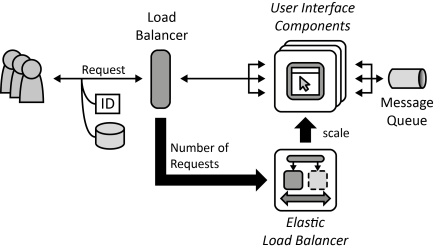", "Driving Question": "How can User Interface Components be accessed interactively by humans while being configurable and decoupled from the remaining application?"}', 'https://www.cloudcomputingpatterns.org/icons/user_interface_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p37, 'Processing Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/processingComponent', '{"Icon": "", "Intend": "Possibly long running processing functionality is handled by separate components to enable elastic scaling. Processing functionality is further made configurable to support different customer requirements.", "Context": "The processing functionality offered by an application shall be handled by different application component instances that operate independently. Instances of these components have to be added and removed easily to the application as part of scaling operations.", "Solution": "Processing functionality is split into separate function blocks and assigned to independent Processing Components. Each processing component is scaled out independently and is implemented in a stateless fashion as described in the Stateless Component pattern. Scaling is handled by an Elastic Queue. Data required for processing is provided with requests or by Storage Offerings.", "Solution Sketch": "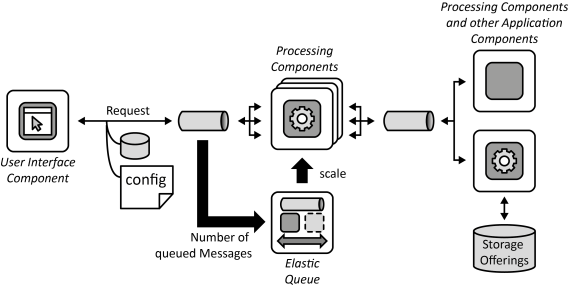", "Driving Question": "How can processing be scaled out elastically among distributed resources while being configurable regarding the supported functions to meet different customers’ requirements?"}', 'https://www.cloudcomputingpatterns.org/icons/processing_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p38, 'Batch Processing Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/batchProcessingComponent', '{"Icon": "", "Intend": "Requests are delayed until environmental conditions make their processing feasible.", "Context": "Distributed Applications assing processing functionality to different components to them independently. If such Processing Components are accessed asynchronously, certain conditions may make it unfeasible to process the requests immediately: seldom accesses to processing functionality, powerful Processing Component instances accessed continuously, and environmental conditions, such as resource costs.", "Solution": "Asynchronous processing requests are accepted at all times, but stored them until conditions are optimal for their processing. Based on the number of stored requests, environmental conditions, and custom rules, components are instantiated to handle the requests. Requests are only processed under non-optimal conditions if they cannot be delayed any longer.", "Solution Sketch": "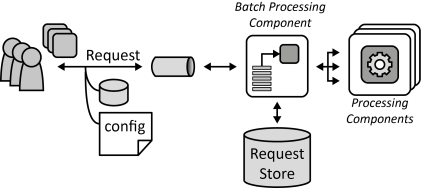", "Driving Question": "How can asynchronous processing requests be delayed to be handled when conditions for their processing are optimal?"}', 'https://www.cloudcomputingpatterns.org/icons/batch_processing_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p39, 'Data Access Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/dataAccessComponent', '{"Icon": "", "Intend": "Functionality to store and access data elements is provided by special components that isolate complexity of data access, enable additional data consistency, and ensure adjustability of handled data elements to meet different customer requirements.", "Context": "Handling the complexity of accessing data, i.e., handling of authorization, querying for data, failure handling etc. tightly couples application components to the used storage offering and complicates the implementation of these components as a lot of the idiosyncrasies of data handling have to be respected by them. Instead, different data sources should be integrated to provide a unified data access to other application components. Also, data may be stored at different cloud providers that have to be integrated as well.", "Solution": "Access to different data sources is integrated by a Data Access Component. This component coordinates all data manipulation. In case a storage offering shall be replaced or the interface of a storage offering changes, the Data Access Component is the only component that has to be adjusted.", "Solution Sketch": "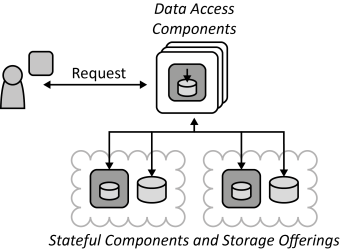", "Driving Question": "How can the complexity of data storage due to access protocols and data consistency be hidden and isolated while ensuring data structure configurability?"}', 'https://www.cloudcomputingpatterns.org/icons/data_access_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p40, 'Data Abstractor', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/dataAbstractor', '{"Icon": "", "Intend": "The data provided to users or other application components is abstracted to inherently support eventually consistent data storage through the use of abstractions and approximations.", "Context": "If a Distributed Application using eventually consistent Storage Offerings is designed for consistent data, data consistency could be reassured by application components, such as the Data Access Component. However, this can void the benefits introduced by eventually consistency regarding performance and availability.", "Solution": "The style of data representation is adjusted to allow retrieved data to be eventually consistent. The data representation always reflects that the consistent state is unknown by approximating values or abstracting them into more general ones, such as progress bars, traffic lights, or change tendencies (increase / decrease).", "Solution Sketch": "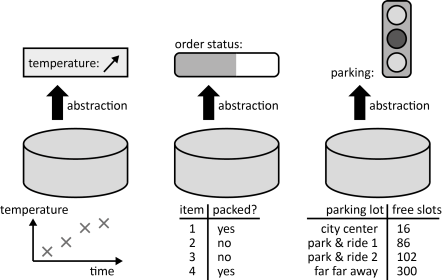", "Driving Question": "How can eventually consistent data be presented, so that possible inconsistencies are hidden from other application components and application users?"}', 'https://www.cloudcomputingpatterns.org/icons/data_abstractor_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p41, 'Idempotent Processor', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/idempotentProcessor', '{"Icon": "", "Intend": "Application functions detect duplicate messages and inconsistent data or are designed to be immune to these conditions.", "Context": "In case of Storage Offerings displaying Eventual Consistency, application components can possibly read obsolete information that has already been processed. Still, the component may choose to process the data again as changes cannot be seen. The same problem arises, if application components of a Distributed Application exchange information asynchronously via a Message-oriented Middleware assuring At-least-once Delivery. In this case duplicate messages can lead to duplicate processing.", "Solution": "The Idempotent Processor ensures that duplicate messages and inconsistent data do not affect application functionality either through inconsistency detection identifying message duplicates and data inconsistencies or through idempotent semantics of application functions enabling them to be erroneously executed multiple times with the same outcome.", "Solution Sketch": "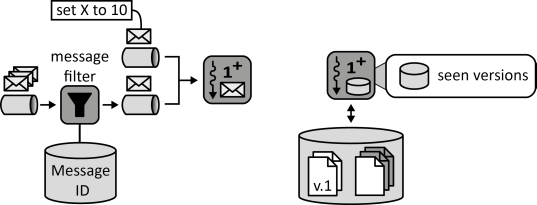", "Driving Question": "How can an application component cope with message duplicates or data inconsistencies that could lead to duplicate function execution?"}', 'https://www.cloudcomputingpatterns.org/icons/idempotent_processor_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p42, 'Transaction-based Processor', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/transaction-basedProcessor', '{"Icon": "", "Intend": "Components receive messages or read data and process the obtained information under a transactional context to ensure that all received messages are processes and all altered data is consistent after processing, respectively.", "Context": "A Message-oriented Middleware can use Transaction-based Delivery of messages to ensure that messages are received successfully by a client. However, using this approach no assurances can be made regarding the processing of that received message.", "Solution": "Transaction-based Delivery subsumes reading the message from a queue and deleting it from a queue in one transaction. The Transaction-based Processor extends the transactional context to the processing of the message in the receiver. Analogous, if interacting with a storage offering, the Transaction-based Processor reads, processes and writes data in one transactional context.", "Solution Sketch": "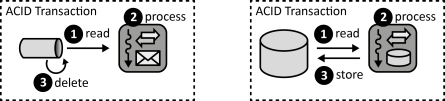", "Driving Question": "How can an application component ensure that all messages it receives are processed successfully and altered data is persisted successfully after processing?"}', 'https://www.cloudcomputingpatterns.org/icons/transaction_based_processor_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p43, 'Timeout-based Message Processor', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/timeout-basedMessageProcessor', '{"Icon": "", "Intend": "Clients acknowledge message receptions and processing to ensure that all messages are handled by an application. If a message is not acknowledged after a certain timeout, it is processed by a different client.", "Context": "A Message-oriented Middleware uses Timeout-based Delivery to ensure that messages are received successfully by at least one client. Additionally, it shall be assured by the application that a message has also been properly processed after its reception.", "Solution": "Instead of sending an acknowledgement right after receiving a message, a timeout-based message processor sends this acknowledgement after it has successfully processed the message.", "Solution Sketch": "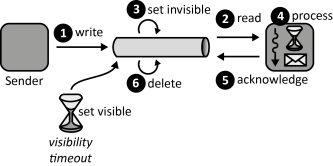", "Driving Question": "How can an application process messages while guaranteeing that all messages handled by the application are processed at-least-once?"}', 'https://www.cloudcomputingpatterns.org/icons/timeout_based_message_processor_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p44, 'Multi-Component Image', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/multi-componentImage', '{"Icon": "", "Intend": "Virtual servers host multiple application components that may not be active at all times to reduce provisioning and decommissioning operations.", "Context": "A Distributed Application may deploy its application components among virtual servers provided by an Elastic Infrastructure. The individual application components may, however, not fully utilize the servers if only one component is hosted per server. Therefore, mapping each application component to a single server may lead to underutilization.", "Solution": "Multiple application components (possibly including middleware) are hosted on a single virtual server to ensure that running virtual servers may be used for different purposes without making provisioning or decommissioning operations necessary.", "Solution Sketch": "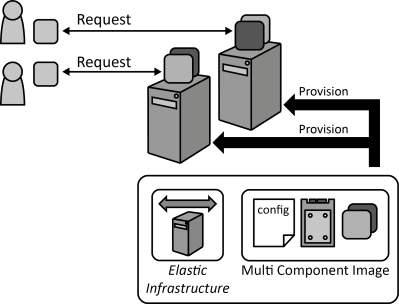", "Driving Question": "How can a virtual server provide the functionality of multiple application components to be used flexibly in applications?"}', 'https://www.cloudcomputingpatterns.org/icons/multi_component_image_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p45, 'Shared Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/sharedComponent', '{"Icon": "", "Intend": "A component is accessed by multiple tenants to leverage economies of scale.", "Context": "A Distributed Application is offered to multiple tenants. These tenants share IT resources required by applications provided to them. The provisioning of application component instances shall be optimized by limiting the portion of the application stack and the number of application components deployed exclusively for one tenant.", "Solution": "A Shared Component provides functionality that is equal for all tenants accessing the component. All tenants can be treated as a uniform user group to which a common user experience and service level is guaranteed.", "Solution Sketch": "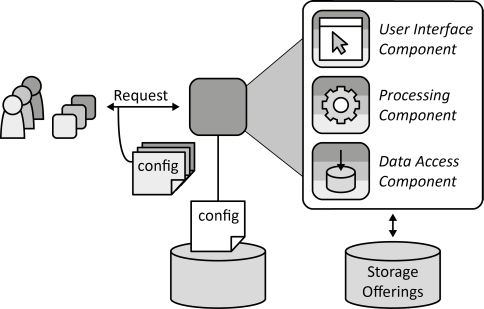", "Driving Question": "How can an application component be shared between multiple tenants enabling some individual configuration?"}', 'https://www.cloudcomputingpatterns.org/icons/shared_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p46, 'Tenant-isolated Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/tenant-isolatedComponent', '{"Icon": "", "Intend": "A component shared between tenants avoids influences between tenants regarding assured performance, available storage capacity, and accessibility of functionality and data.", "Context": "A Distributed Application is offered to multiple tenants. These tenants share IT resources required by applications provided to them. However, the sharing of application components is hindered by three factors. First, tenants may have unique requirements and, thus, expect application components to be configurable to their individual needs. Second, tenants may not trust each other. Third, tenants expect an application to behave as if a single tenant was the only one accessing it.", "Solution": "Components on all layers of the application stack are specifically developed to be used by different tenants. Especially, they ensure isolation between tenants by controlling tenant access, processing performance used, and separation of stored data.", "Solution Sketch": "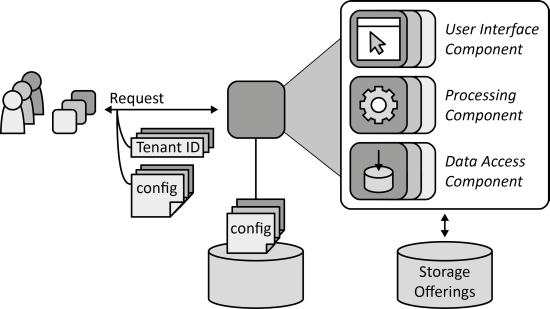", "Driving Question": "How can an application component be shared between multiple tenants enabling individual configuration and tenant-isolation regarding performance, data volume, and access privileges?"}', 'https://www.cloudcomputingpatterns.org/icons/tenant_isolated_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p47, 'Dedicated Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/dedicatedComponent', '{"Icon": "", "Intend": "Components providing critical functionality shall be provided exclusively to tenants while still allowing other components to be shared between tenants.", "Context": "A Distributed Application is offered to multiple tenants. These tenants share IT resources required by applications provided to them.", "Solution": "Dedicated application components are provided exclusively for each tenant using the application.", "Solution Sketch": "", "Driving Question": "How can application components that cannot be shared be integrated into a multi-tenant application?"}', 'https://www.cloudcomputingpatterns.org/icons/dedicated_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p48, 'Restricted Data Access Component', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/restrictedDataAccessComponent', '{"Icon": "", "Intend": "Data provided to clients from different environments is adjusted based on access restrictions.", "Context": "A Distributed Application may host application components at different providers to match the individual requirements of components with best fitting providers. One factor may be that application components experience different workload. Other differentiating factors of the used environments may be assured privacy, security, and trust. These differences may, however, impact the data that may be accessible in an environment.", "Solution": "Data storage restrictions and access privileges are defined for each data element. Access to these data elements is provided by separate Restricted Data Access Components that interpret the information associated with data elements. It adjusts data accordingly through deletion or obfuscation during every access.", "Solution Sketch": "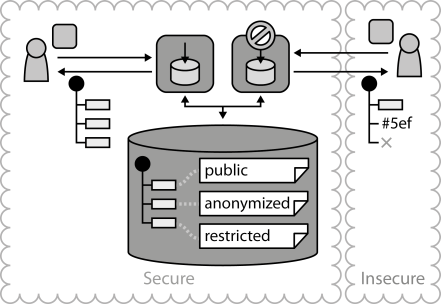", "Driving Question": "How can an application component alter provided data based on access restrictions imposed on different environments?"}', 'https://www.cloudcomputingpatterns.org/icons/restricted_data_access_component_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p49, 'Message Mover', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/messageMover', '{"Icon": "", "Intend": "Messages are moved automatically between different cloud providers to provide unified access to application components using messaging.", "Context": "The application components comprising a Distributed Application often exchange data using messages. If used message queues reside in different cloud environments that form a Hybrid Cloud accessibility to queues of one environment may be restricted for application components that are deployed in another environment.", "Solution": "A Message Mover is used to integrate message queues hosted in different environments by receiving messages from one queue and transferring it to a queue in other environments.", "Solution Sketch": "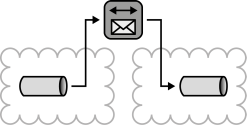", "Driving Question": "How can message queues of different providers be integrated without an impact on the application components using them?"}', 'https://www.cloudcomputingpatterns.org/icons/message_mover_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p50, 'Application Component Proxy', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/applicationComponentProxy', '{"Icon": "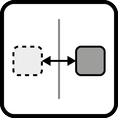", "Intend": "An application component is made available in an environment from where it cannot be accessed directly by deploying an Application Component Proxy. The communication between this proxy and the application component is initiated and maintained from the environment where communication is unrestricted.", "Context": "Application components of a Distributed Application are deployed in different Cloud Environments that form a Hybrid Cloud. These environments often have different privacy, security, and trust properties. The communication between environments is often restricted through the use of firewalls. However, application components hosted in unrestricted environments may have to access application components hosted in a restricted environment.", "Solution": "The interface of a restricted application component is duplicated to form a proxy component. Synchronous and asynchronous communication with this proxy component is initiated and maintained from the restricted environment that may access the unrestricted environment directly.", "Solution Sketch": "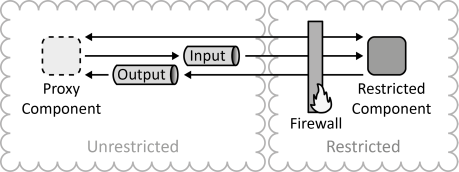", "Driving Question": "How can an application component be accessed if direct access to its hosting environment is restricted?"}', 'https://www.cloudcomputingpatterns.org/icons/application_component_proxy_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p51, 'Compliant Data Replication', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/compliantDataReplication', '{"Icon": "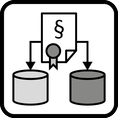", "Intend": "Data is replicated among multiple environments that may handle different data subsets. During replication data is obfuscated and deleted depending on laws and security regulations. Data updates are adjusted automatically to reflect the different data structures handled by environments.", "Context": "Distributed Applications that are hosted in a Hybrid Cloud often require access to the same data from different application components. If application components accessing the data are globally distributed, data access performance may be reduced drastically if data is only stored in one geographic location. Therefore, data may have to be replicated. Due to laws and corporate regulations, some of these locations may only handle a subset of the available data or data has to be obfuscated.", "Solution": "Data replicas in different environments are updated asynchronously using messaging. Message filters are used to delete and obfuscate certain data elements in these messages as they leave the trusted environment. Information about the data manipulations stored in a storage offering. If data is then altered in the less secure environment, the corresponding update message is enriched by a message enricher as it enters the secure environment.", "Solution Sketch": "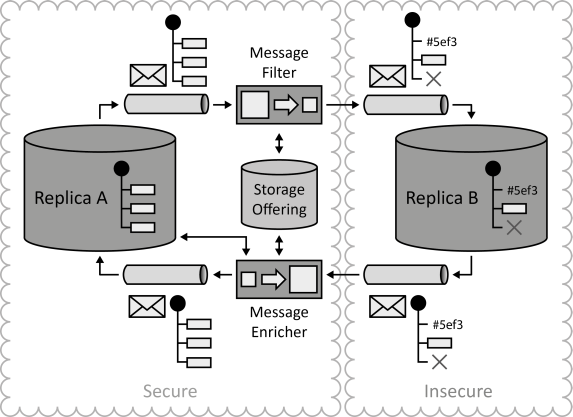", "Driving Question": "How can data be replicated between environments if some environments may only handle subsets of the data due to laws and corporate regulations?"}', 'https://www.cloudcomputingpatterns.org/icons/compliant_data_replication_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p52, 'Integration Provider', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/integrationProvider', '{"Icon": "", "Intend": "Integration functionality such as messaging and shared data is hosted by a separate provider to enable integrate of otherwise separated hosting environments.", "Context": "When companies collaborate or one company has to integrate applications of different regional offices, different applications or the components of a Distributed Application are distributed among different hosting environments. Communication between these environments may be restricted and enabling communication may be hindered by corporate regulations.", "Solution": "The Distributed Applications or their components communicate using integration components offered by a third party provider.", "Solution Sketch": "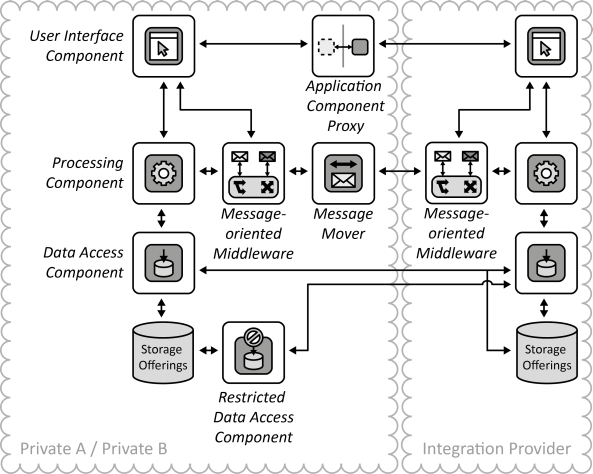", "Driving Question": "How can application components that reside in different environments, possibly belonging to different companies, be integrated through a third-party provider?"}', 'https://www.cloudcomputingpatterns.org/icons/integration_provider_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p53, 'Provider Adapter', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/providerAdapter', '{"Icon": "", "Intend": "Provider interfaces are encapsulated and mapped to unified interfaces used in applications to separate concerns of interactions with the provider from application functionality.", "Context": "Cloud providers offer many interfaces that can be used in application components of a Distributed Application. If a component directly interacts with these interfaces, its implementation becomes strongly interleaved with the specific functions offered and the protocols used.", "Solution": "The Provider Adapter encapsulates all provider-specific implementations required for authentication, data formatting etc. in an abstract interface. The Provider Adapter , thus, ensures separation of concerns between application components accessing provider functionality and application components providing application functionality. It may also offer synchronous provider-interfaces to be accessed asynchronously via messages and vice versa.", "Solution Sketch": "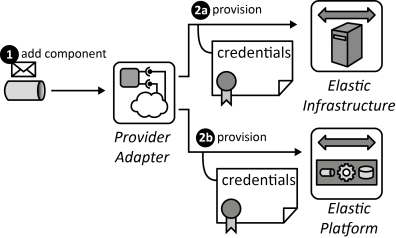", "Driving Question": "How can the dependencies of an application component on a provider-specific interface be managed?"}', 'https://www.cloudcomputingpatterns.org/icons/provider_adapter_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p54, 'Managed Configuration', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/managedConfiguration', '{"Icon": "", "Intend": "Scaled-out application components should use a centrally stored configuration to provide a unified behavior that can be adjusted simultaneously.", "Context": "Application components of a Distributed Application often have configuration parameters. Storing configuration information together with the application component implementation can be unpractical as it results in more overhead in case of configuration changes. Each running instance of the application component must be updated separately. Component images stored in Elastic Infrastructures or Elastic Platforms also have to be updated upon configuration change.", "Solution": "Configurations are stored in a central Storage Offering, commonly, a Relational Database, Key-Value Storage, or Blob Storage from where it is accessed by all running component instances either by accessing the storage periodically or by sending messages to the components.", "Solution Sketch": "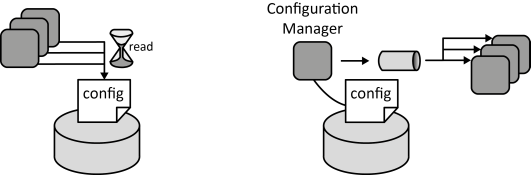", "Driving Question": "How can the configuration of scaled out application component instances be controlled in a coordinated fashion?"}', 'https://www.cloudcomputingpatterns.org/icons/managed_configuration_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p55, 'Elasticity Manager', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticityManager', '{"Icon": "", "Intend": "The utilization of IT resources on which an elastically scaled-out application is hosted, for example, virtual servers is used to determine the number of required application component instances.", "Context": "Application components of a Distributed Application hosted on an Elastic Infrastructure or Elastic Platform shall be scaled-out. The instances of applications components, thus, shall be provisioned and decommissioned automatically based on the current workload experienced by the application.", "Solution": "The utilization of cloud resources on which application component instances are deployed is monitored. This could be, for example, the CPU load of a virtual server. This information is used to determine the number of required instances.", "Solution Sketch": "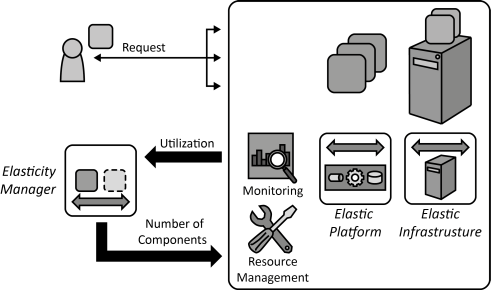", "Driving Question": "How can the number of required application component instances be determined based on the utilization of hosting IT resources?"}', 'https://www.cloudcomputingpatterns.org/icons/elasticity_manager_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p56, 'Elastic Load Balancer', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticLoadBalancer', '{"Icon": "", "Intend": "The number of synchronous accesses to an elastically scaled-out application is used to determine the number of required application component instances.", "Context": "Application components of a Distributed Application shall be scaled out automatically. Requests sent to an application shall be used as an indicator for the currently experienced workload from which the required number of components instances shall be deducted.", "Solution": "Based on the number of synchronous requests handled by a load balancer and possibly other utilization information, the required number of required component instances is determined.", "Solution Sketch": "", "Driving Question": "How can the number of required application component instances be determined based on monitored synchronous accesses?"}', 'https://www.cloudcomputingpatterns.org/icons/elastic_load_balancer_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p57, 'Elastic Queue', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticQueue', '{"Icon": "", "Intend": "The number of asynchronous accesses via messaging to an elastically scaled-out application is used to adjust the number of required application component instances.", "Context": "A Distributed Application is comprised of multiple application components that are accessed asynchronously and deployed to an Elastic Infrastructure or an Elastic Platform. The required provisioning and decommissioning operations to scale this application should be performed in an automated fashion.", "Solution": "Queues that are used to distribute asynchronous requests among multiple application components instances are monitored. Based on the number of enqueued messages the Elastic Queue adjusts the number of application component instances handling these requests.", "Solution Sketch": "", "Driving Question": "How can the number of required application component instances be adjusted based on monitored asynchronous accesses?"}', 'https://www.cloudcomputingpatterns.org/icons/elastic_queue_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p58, 'Watchdog', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/watchdog', '{"Icon": "", "Intend": "Applications cope with failures automatically by monitoring and replacing application component instances if the provider-assured availability is insufficient.", "Context": "If a Distributed Application is comprised of many application components it is dependent on the availability of all component instances. To enable high availability under such conditions, applications have to rely on redundant application component instances and the failure of these instances has to be detected and coped with automatically.", "Solution": "Individual application components rely on external state information by implementing the Stateless Component pattern. Components are scaled out and multiple instances of them are deployed to redundant resources. The component instances are monitored by a separate Watchdog component and replaced in case of failures.", "Solution Sketch": "", "Driving Question": "How can applications automatically detect failing application components and handle their replacement?."}', 'https://www.cloudcomputingpatterns.org/icons/watchdog_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p59, 'Elasticity Management Process', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/elasticityManagementProcess', '{"Icon": "", "Intend": "Application component instances are added automatically to an application to cope with increasing workload. If the workload decreases application component instances are removed respectively.", "Context": "A Distributed Application uses Elasticity Managers, Elastic Queues, or Elastic Load Balancers to ensure an elastic scaling of application components. To handle this task adequately, the current resource demand has to be obtained automatically from the application and has to be reflected in provisioning and decommissioning of cloud resources.", "Solution": "An Elasticity Management Process analyzes the utilization of application component instances in intervals, when a system manager requests it, or if certain conditions are observed by the monitoring component. Based on this information, the current workload of the application is computed and reflected by adjusting used resources.", "Solution Sketch": "", "Driving Question": "How can the number of resources to which application components are scaled-out be adjusted efficiently to the currently experienced workload and anticipated future workload?"}', 'https://www.cloudcomputingpatterns.org/icons/elasticity_management_process_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p60, 'Feature Flag Management Process', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/featureFlagManagementProcess', '{"Icon": "", "Intend": "If the cloud cannot provide required resources in time, the features provided by application components are degraded gracefully to replace or disable unimportant ones in order to keep vital features operational.", "Context": "While the elasticity of clouds generally allows a tight alignment of resource numbers to the experienced workload, the time it takes to provision new resources remains as a limiting factor. If the workload increases too drastically, it may take too long to provision new resources. Furthermore, cloud providers often do not guarantee concrete provisioning times.", "Solution": "Less important application functionality provided by application component instances is disabled or replaced with a less demanding implementation, if the cloud provider cannot fulfill current workload demands. When resources can eventually be provisioned again, the application components return to normal operation.", "Solution Sketch": "", "Driving Question": "How can the performance of an application degrade gracefully, if the experienced workload increases but additional cloud resources are unavailable or take too long to provision?"}', 'https://www.cloudcomputingpatterns.org/icons/feature_flag_management_process_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p61, 'Update Transition Process', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/updateTransitionProcess', '{"Icon": "", "Intend": "When a new application component version, middleware versions etc. become available, running application components are updated seamlessly.", "Context": "During the runtime of a Distributed Application, new versions of used middleware, operating systems, or application components may become available. A seamless switch from the old to the new version of application components shall be enabled.", "Solution": "The new component version is created. Additional application component instances of the new version are provisioned. These components are executed simultaneously with the application components of the old version. If necessary, load balancing is then switched to the component instances of the new version. If the application components access a queue, this step is unnecessary. Finally, the old application component instances are decommissioned.", "Solution Sketch": "", "Driving Question": "How can application components of a Distributed Application be updated seamlessly?"}', 'https://www.cloudcomputingpatterns.org/icons/update_transition_process_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p62, 'Standby Pooling Process', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/standbyPoolingProcess', '{"Icon": "", "Intend": "Application component instances should be kept on standby to increase provisioning speed and utilize billing time-slots efficiently.", "Context": "Even though application component instances may be provisioned and decommissioned dynamically, it usually requires some time to actually provision and decommission them. If a cloud application, however, experiences drastic and quick workload changes, these provisioning times may limit its capability to obtain the required resources quickly enough. Decommissioning of component instances immediately when no longer needed may also be ineffective, if cloud resources are charged for fixed time-slots.", "Solution": "Instead of decommissioning application component instances instantly when they are unused, they are assigned to a standby list They are decommissioned only when the time-slot they have been paid for has been utilized and they are still not needed. The standby list may always contain a certain number of component instances to ensure timely provisioning.", "Solution Sketch": "\n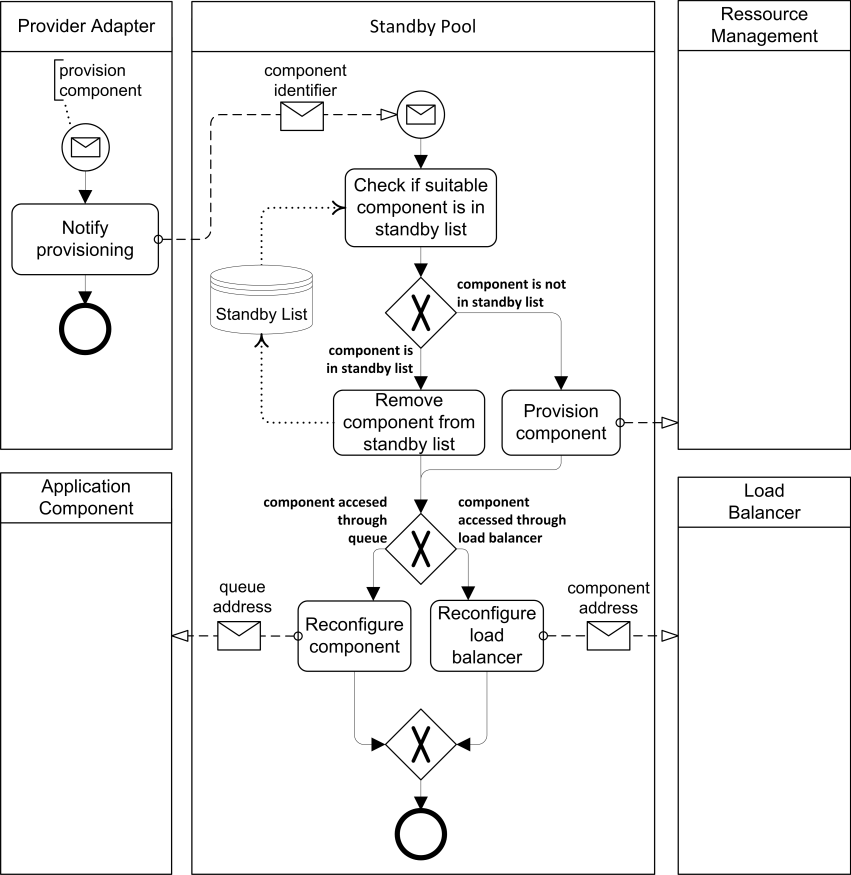", "Driving Question": "How can defined provisioning times for application component instances be ensured while utilizing pay-per-use resources in an optimal fashion?"}', 'https://www.cloudcomputingpatterns.org/icons/standby_pooling_process_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p63, 'Resiliency Management Process', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/resiliencyManagementProcess', '{"Icon": "", "Intend": "Application components are checked for failures and replaced automatically without human intervention.", "Context": "A Watchdog allows to monitor application components and react to failures. To handle this task, the component functionality must be verified and failing components must be replaced with newly provisioned components in a coordinated fashion.", "Solution": "This process is triggered by the monitoring functionality or by the Watchdog if it detects a component failure. Additionally, the Resiliency Management Process periodically verifies application component health. If a failure is detected, the faulty application component instance is decommissioned and replaced by a newly provisioned instance.", "Solution Sketch": "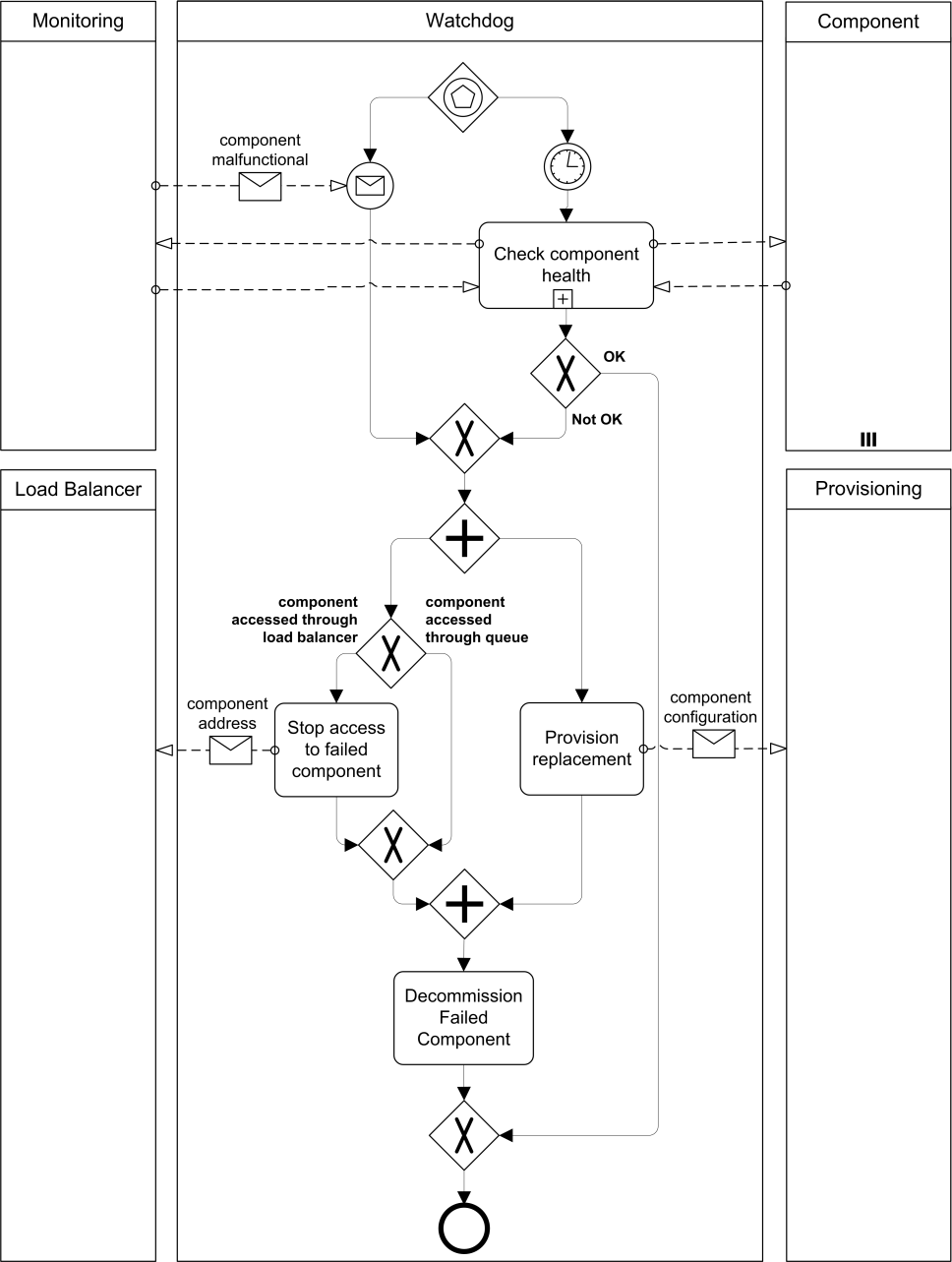", "Driving Question": "How can the overall availability of an application be ensured automatically even if individual application component instances fail?"}', 'https://www.cloudcomputingpatterns.org/icons/resiliency_management_process_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p64, 'Two-Tier Cloud Application', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/two-tierCloudApplication', '{"Icon": "", "Intend": "Presentation and business logic is bundled to one stateless tier that is easy to scale. This tier is separated from the data tier that is harder to scale and often handled by a provider-supplied storage offering.", "Context": "A Distributed Application is decomposed into application components to scale individual application functions independently. In this scope, data handling functionality is significantly harder to scale than Stateless Components, because Stateful Components have to coordinate state information between instances. Therefore, the application shall be decomposed in a fashion that separates the easy-to-scale functionality from the hard-to-scale functionality.", "Solution": "Application functionality is decomposed into data handling functionality, provided by one or several Storage Offerings, and application components handling presentation and business logic. This separation enables the two tiers to elastically scale independently with their workloads.", "Solution Sketch": "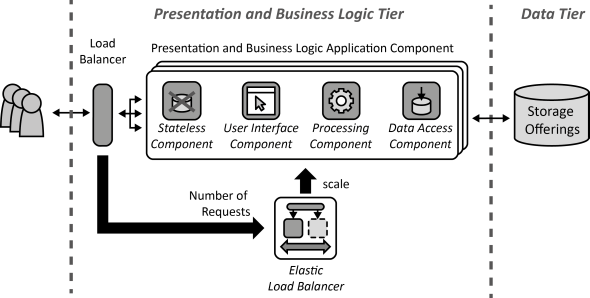", "Driving Question": "How can application functionality be separated from data handling to scale them independently?"}', 'https://www.cloudcomputingpatterns.org/icons/two_tier_cloud_application_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p65, 'Hybrid Data', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridData', '{"Icon": "", "Intend": "Data of varying size is hosted in an elastic cloud while the remainder of an application resides in a static environment.", "Context": "A Distributed Application handles data whose size varies drastically over time. Large amounts of data may, thus, be generated periodically and are then deleted again, may increase and decrease randomly, or may display a general increase or decrease over time. Especially, during these changes, the user number and their accesses to the application can be static resulting in Static Workload on the remainder of the application components.", "Solution": "Data whose varying size makes it unsuitable for hosting in a static environment is handled by Storage Offerings in an elastic cloud. At this location data is either accessed by Data Access Components that are hosted in the static environment or by Data Access Components hosted in the elastic environment.", "Solution Sketch": "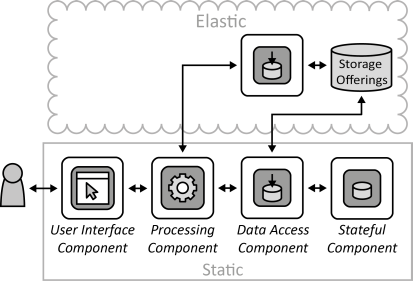", "Driving Question": "How can a data handling functionality that experiences varying workload be hosted in an elastic cloud while the rest of the application is located in a static data center?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_data_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p66, 'Three-Tier Cloud Application', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/three-tierCloudApplication', '{"Icon": "", "Intend": "The presentation, business logic, and data handling is realized as separate tiers to scale stateless presentation and compute-intensive processing independently of the data tier, which is harder to scale and often handled by the cloud provider.", "Context": "A Distributed Application is decomposed into application components to scale individual application functions independently. There can be many differentiating factors of application tiers. For example, if Processing Components are more computation intensive or are used less frequently than User Interface Components, aligning the elastic scaling of these two components by summarizing their implementation in one tier can be inefficient. This issue arises every time components experiences different Application Workloads. The number of provisioned component instances cannot be aligned well to the different workloads if they are summarized to coarse grained tiers.", "Solution": "The application is decomposed into three tiers, where each tier is elastically scaled independently. The presentation tier is comprised of a load balancer and an application component that implements the Stateless Component pattern and User Interface Component pattern. The business logic tier is comprised of an application component implementing the Stateless Component pattern in addition to the Processing Component pattern.", "Solution Sketch": "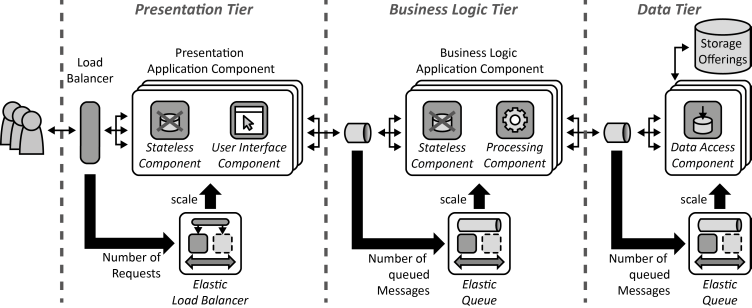", "Driving Question": "How can presentation logic, business logic, and data handling be decomposed into separate tiers that are scaled independently?"}', 'https://www.cloudcomputingpatterns.org/icons/three_tier_cloud_application_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p67, 'Content Distribution Network', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/contentDistributionNetwork', '{"Icon": "", "Intend": "Applications component instances and data handled by them are globally distributed to meet the access performance required by a global user group.", "Context": "If the application provides multimedia content to users, for example, streamed videos and music the amount of data to be served increases drastically. If such multimedia content is located too far from the user accessing it, the communication delay of the distribution network may hinder the timely access to data. Therefore, storing content in only one centralized location, i.e., one cloud or data center is unfeasible.", "Solution": "Content replicas are established in different physical locations of one or multiple clouds. During this distribution of replicas, the topology of distribution networks is considered to ensure locality for all users. Replicas are updated from a central location.", "Solution Sketch": "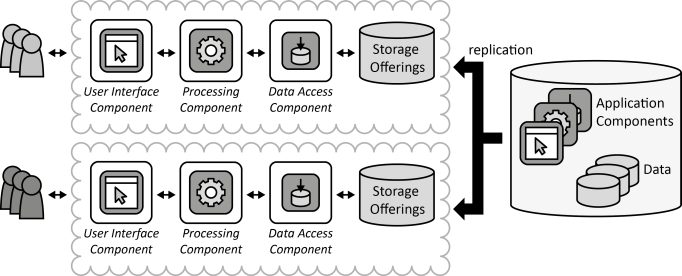", "Driving Question": "How can timely access to an application be ensured for a globally distributed user group?"}', 'https://www.cloudcomputingpatterns.org/icons/content_distribution_network_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p68, 'Hybrid User Interface', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridUserInterface', '{"Icon": "", "Intend": "Varying workload from a user group interacting asynchronously with an application is handled in an elastic environment while the remainder of an application resides in a static environment.", "Context": "An application serves user groups with different workload behavior. One user group generates Static Workload, while another user group generates Periodic Workload, Once-in-a-lifetime Workload, Unpredictable Workload, or Continuously Changing Workload. Since the predictability of the user group size and workload behavior differs, it shall be ensured that unexpected peak workloads do not affect the performance of the application while each user group is handled by the most suitable cloud environment.", "Solution": "The User Interface Component serving users generating varying workload is hosted in an elastic cloud environment. Other application components that are hosted in a static environment. The user interface deployed in the elastic cloud is integrated with the remainder of the application in a decoupled fashion using messaging to ensure Loose Coupling.", "Solution Sketch": "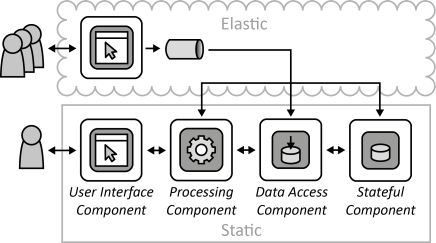", "Driving Question": "How can a user interface for asynchronous interaction be hosted in a cloud while being integrated with an application otherwise hosted in a static data center?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_user_interface_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p69, 'Hybrid Processing', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridProcessing', '{"Icon": "", "Intend": "Processing functionality that experiences varying workload is hosted in an elastic cloud while the remainder of an application resides in a static environment.", "Context": "A Distributed Application provides processing functionality that experience different workload behavior. The user group accessing the application is, thus, predictable in size, but accesses the functions provided by the application differently. While most of the functions are used equally over time and, therefore, experience Static Workload, some Processing Components experience Periodic Workload, Unpredictable Workload, or Continuously Changing Workload.", "Solution": "The Processing Components experiencing varying workloads are provisioned in an elastic cloud. Loose Coupling is ensured by exchanging information between the hosting environments asynchronously via messages.r your input for this section here.", "Solution Sketch": "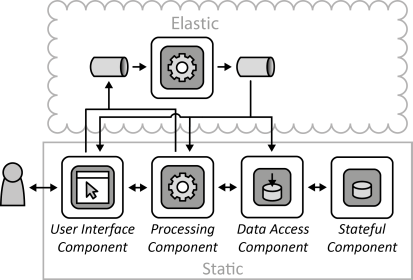", "Driving Question": "How can Processing Components that experiences varying workload be hosted in an elastic cloud while the remainder of an application is hosted in a static data center?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_processing_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p70, 'Hybrid Backup', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridBackup', '{"Icon": "", "Intend": "Data is periodically extracted from an application to be archived in an elastic cloud for disaster recovery purposes.", "Context": "Many applications are used by small and medium businesses which do not have the required IT skills to host and maintain their own highly available infrastructure. Especially, requirements regarding business resiliency – the ability to recover from an error – and business continuity – the ability to operate during an error – are challenging. Furthermore, there are laws and regulations making businesses liable to archive data and keep it accessible for audits, often over very long periods of time.", "Solution": "A Distributed Application is hosted in a local static environment of the company. Data handled by Stateful Components is periodically extracted and replicated to a cloud storage offering.", "Solution Sketch": "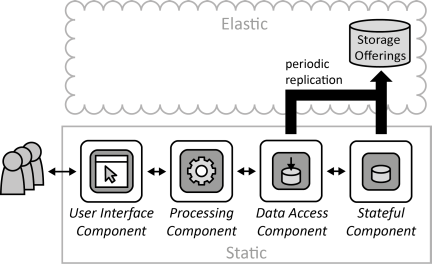", "Driving Question": "How can data be archived in a remote environment while the remainder of the application is hosted in a static environment?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_backup_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p71, 'Hybrid Backend', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridBackend', '{"Icon": "", "Intend": "Backend functionality comprised of data intensive processing and data storage is experiencing varying workloads and is hosted in an elastic cloud while the rest of an application is hosted in a static data center.", "Context": "A Distributed Application provides processing functionality that experiences varying workload behavior. Mainly, Static Workload has to be handled, but some Processing Components experience Periodic Workload, Unpredictable Workload, or Continuously Changing Workload. Application components providing the respective processing functionality experiencing varying workload should, therefore, be hosted in an elastic environment. However, these components have to access large amounts of data during their execution making them highly dependent on the availability and the timely access to such data.", "Solution": "The Processing Components experiencing varying workloads are hosted in an elastic cloud together with the data accessed during their operation. Processing Components in the elastic cloud are triggered from the static environment through asynchronous messages exchanged via message queues provided by a Message-oriented Middleware. A Data Access Component in the static environment ensures that data required by elastic Processing Components is stored in Storage Offerings The location where this data is stored may then be passed to the elastic Processing Components during their enactment via messages. Data that is not required by the backend functionality may still be stored in Stateful Components hosted in the static data center.", "Solution Sketch": "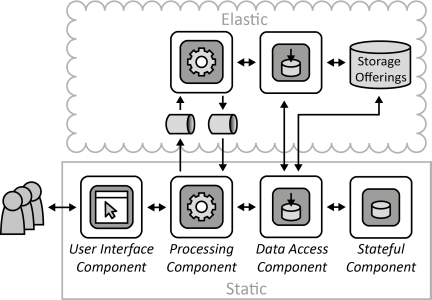", "Driving Question": "How can Processing Components that experience varying workload and need access to large amounts of data be hosted in an elastic environment while the remainder of the application is hosted in a static environment?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_backend_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p72, 'Hybrid Application Functions', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridApplicationFunctions', '{"Icon": "", "Intend": "Some application functionality provided by user interfaces, processing, and data handling is experiencing varying workload and is hosted in an elastic cloud while other application functionality of the same type is hosted in a static environment.", "Context": "Application components comprising a Distributed Application experience varying workloads on all layers of the application stack: User Interface Components, Processing Components, and Data Access Components. All of these components provide functionality to the user group of the application, but this user group accesses functionality differently. In addition to the workload requirements other issues, such as legal and corporate regulations or requirements on security, privacy, and trust may limit the environments to which an application component may be provisioned.", "Solution": "Application components are grouped regarding similar requirements and are deployed into best fitting environments. Interdependencies between the components are reduced by exchanging data using asynchronous messaging to ensure Loose Coupling. Depending on the accessed function, a load balancer redirects user accesses to the different environments seamlessly.", "Solution Sketch": "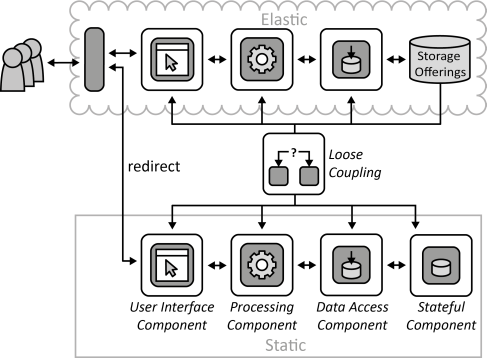", "Driving Question": "How can arbitrary functionality of an application be distributed among static data centers and elastic clouds best matching its requirements?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_application_functions_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p73, 'Hybrid Multimedia Web Application', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridMultimediaWebApplication', '{"Icon": "", "Intend": "Website content is largely provided from a static environment. Multimedia files that cannot be cached efficiently are provided from a large distributed elastic environment for high-performance access.", "Context": "A Distributed Application provides a website accessed by a large globally distributed user group. While most of the website is comprised of static content, there is also a significant amount of multimedia content, such as videos or music that has to be streamed to users.", "Solution": "Static website content is hosted in a static environment from where it is accessed by users. The streaming content is provided by an elastic cloud environment where it is accessed from the application’s User Interface Component. The static content is provided to users’ client software and in this static content, the multimedia content is referenced. Retrieval of this streaming content is often handled directly by the users’ browser software.", "Solution Sketch": "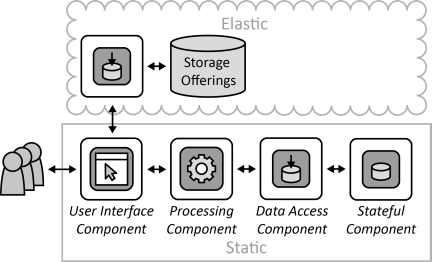", "Driving Question": "How can non-cacheable content be integrated efficiently in a website that is accessed by a large globally distributed user group?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_multimedia_web_application_icon.png', pl_id);
INSERT INTO public.pattern (id, name, uri, content, icon_url, pattern_language_id) VALUES (p74, 'Hybrid Development Environment', 'https://patternpedia.org/patternLanguages/cloudComputingPatterns/hybridDevelopmentEnvironment', '{"Icon": "", "Intend": "A production runtime environment is replicated and mocked in an elastic environment where new applications can be developed and tested.", "Context": "Applications have different requirements on the runtime environment during their development, test, and production phase. During development, hardware requirements are often uncertain, so hardware resources should be flexible to extend resources if necessary. During the test phase, diverse test systems may be needed to verify the proper functioning of the application on different operating systems or when being accessed using different client software, i.e., different browsers. Large numbers of resources may also be required to perform load tests. During the productive use other factors, such as security and availability may be of greater importance than resource flexibility.", "Solution": "The production environment of the application is simulated in the development and test environment through the use of equivalent addressing, similar mocking data, and equivalent functionality provided by the environment. Migration of developed applications is ensured through transformation of application components or compatibility of runtimes. Some testing resources are provided exclusively in the development environment to verify the application behavior under different circumstances.", "Solution Sketch": "", "Driving Question": "How can an application use different computing environments during its development, test, and production stages?"}', 'https://www.cloudcomputingpatterns.org/icons/hybrid_development_environment_icon.png', pl_id);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p11);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p23);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p6, p61);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p18, p18);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p18, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p18, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p19, p19);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p19, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p29);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p1, p26);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p1, p13);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p21, p3);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p21, p30);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p34);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p45);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p46);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p47);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p16, p1);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p16, p21);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p15, p1);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p15, p21);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p23, p1);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p23, p21);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p23, p27);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p23, p38);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p11, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p11, p23);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p11, p1);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p11, p21);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p14);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p24);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p7);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p30);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p19, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p19, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p29, p60);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p31, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p31, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p31, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p1, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p1, p8);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p21, p17);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p21, p14);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p33);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p27, p39);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p16, p27);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p15, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p11, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p26);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p9, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p14);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p10);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p12);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p33);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p41);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p24);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p41);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p7);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p17, p20);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p24, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p24, p63);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p7, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p7, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p7, p63);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p7, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p7, p17);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p3, p8);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p20, p8);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p20, p30);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p20, p42);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p26, p7);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p14, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p10, p20);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p10, p39);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p10, p28);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p13, p8);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p30, p4);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p30, p42);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p30, p5);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p2, p5);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p4, p41);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p4, p25);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p42, p12);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p44, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p44, p63);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p48, p54);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p48, p50);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p15);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p16);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p11);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p23);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p49, p61);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p50, p49);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p50, p33);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p50, p11);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p51, p39);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p51, p71);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p51, p4);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p69);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p38);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p51, p22);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p66);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p51, p2);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p71);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p66);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p52, p64);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p53, p39);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p53, p44);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p53, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p53, p56);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p53, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p12);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p10);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p30);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p56);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p57);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p54, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p56);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p57);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p59);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p53);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p42);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p55, p43);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p56, p59);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p56, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p56, p53);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p57, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p57, p58);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p58, p63);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p58, p55);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p58, p41);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p62);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p60);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p61);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p9);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p17);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p59, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p60, p54);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p61, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p61, p32);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p61, p54);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p62, p63);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p63, p35);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p64, p70);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p64, p67);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p64, p72);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p64, p72);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p64, p65);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p66, p67);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p66, p72);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p68, p69);
INSERT INTO public.directed_edge (id, description, type, pattern_language_id, source_id, target_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', pl_id, p68, p66);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p54, p53, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p56, p56, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p53, p57, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p56, p58, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p42, p58, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p43, p58, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p44, p60, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p62, p60, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p44, p62, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p64, p69, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p64, p66, pl_id);
INSERT INTO public.undirected_edge (id, description, type, p1_id, p2_id, pattern_language_id) VALUES (uuid_generate_v4(), 'null', 'isRelatedTo', p74, p64, pl_id);
END $$;