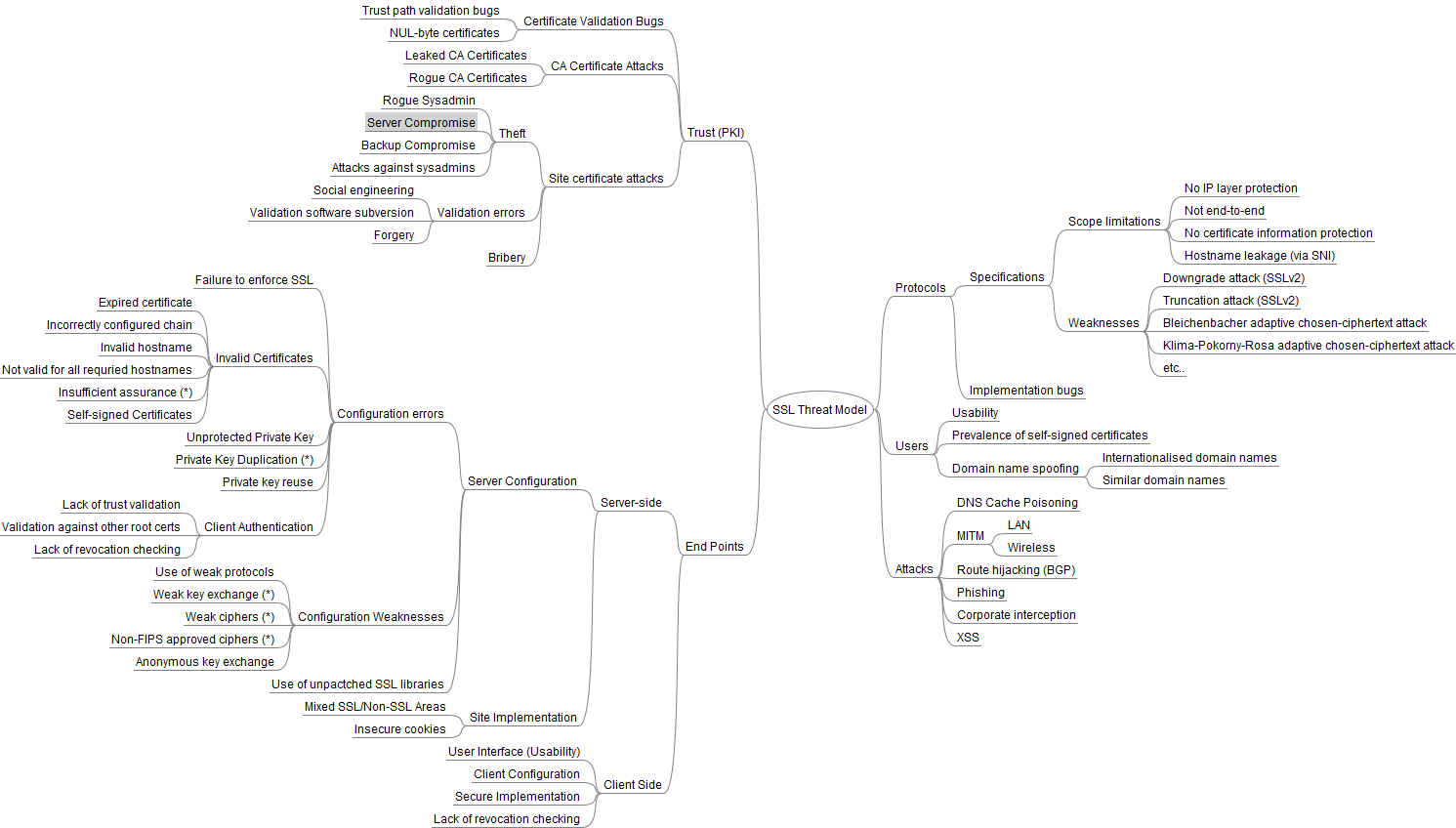
This repository contains various threat model examples for different technologies and systems. These resources can help security professionals, developers, and researchers understand the security risks and best practices for mitigating potential threats in a variety of platforms.
-
OAuth 2.0
OAuth 2.0 Threat Model (RFC 6819) -
DNSSEC, DoT, and DoH
DNSSEC, DoT, and DoH Threat Model -
Web Application
OWASP Threat Modeling Process
-
Kubernetes
-
Docker
-
AWS Fargate
AWS Fargate Threat Modeling - Sysdig
-
Mobile Applications
-
IoT Authentication IoT Authentication Threat Modeling - SAFECode (Page 18)
-
IoT Devices
IoT Devices Security Threat Models - PSA Certified -
Smart Home
Smart Home Threat Model - GitHub
-
PCI DSS
PCI Threat Model - Adam Shostack -
Password Storage Module (PSM)
Secure Password Storage - OWASP -
Certificate Transparency
Certificate Transparency Threat Analysis -
Account Takeover (ATO)
ATO Threat Model Checklist -
Password Managers
Password Manager Threat Model - Stanford (Page 5)
-
AMPS and SNAP Medical Systems
MITRE Playbook for Threat Modeling Medical Devices (Pages 3 and 49) -
ROS 2 Robotic System
-
Web-based User Feedback System
SAFECode Threat Modeling Whitepaper (Page 16) -
Future E-voting System
Swiss Post E-voting Vulnerabilities -
Supply Chain
Supply Chain Threat Modeling Video
-
Cloud Computing
-
OpenStack
- Remote Work
Remote Work Threat Modeling - FireEye
-
CI/CD Pipeline
-
Firmware
Feel free to contribute additional threat model examples or improvements to existing entries. Open a pull request to share your work with the community!
This repository is licensed under the MIT License - see the LICENSE file for details.