Greetings to my fellow Technology Advocates and Specialists.
In this Session, I will demonstrate How to Create Service Connection Using DevOps CLI.
I had the Privilege to talk on this topic in ONE Azure Communities:-
| NAME OF THE AZURE COMMUNITY | TYPE OF SPEAKER SESSION |
|---|---|
| Festive Tech Calendar 2022 | Virtual |
| LIVE RECORDED SESSION:- |
|---|
| LIVE DEMO was Recorded as part of my Presentation in FESTIVE TECH CALENDAR 2022 Forum/Platform |
| Duration of My Demo = 1 Hour 05 Mins 08 Secs |
 |
| USE CASES:- |
|---|
| Create DevOps Service Connection, Prompting PAT (Personal Access Token) |
| Create DevOps Service Connection, Without Prompting PAT (Personal Access Token) |
| AUTOMATION OBJECTIVE:- |
|---|
| Create Service Principal. |
| Query the Application ID of the Service Principal. |
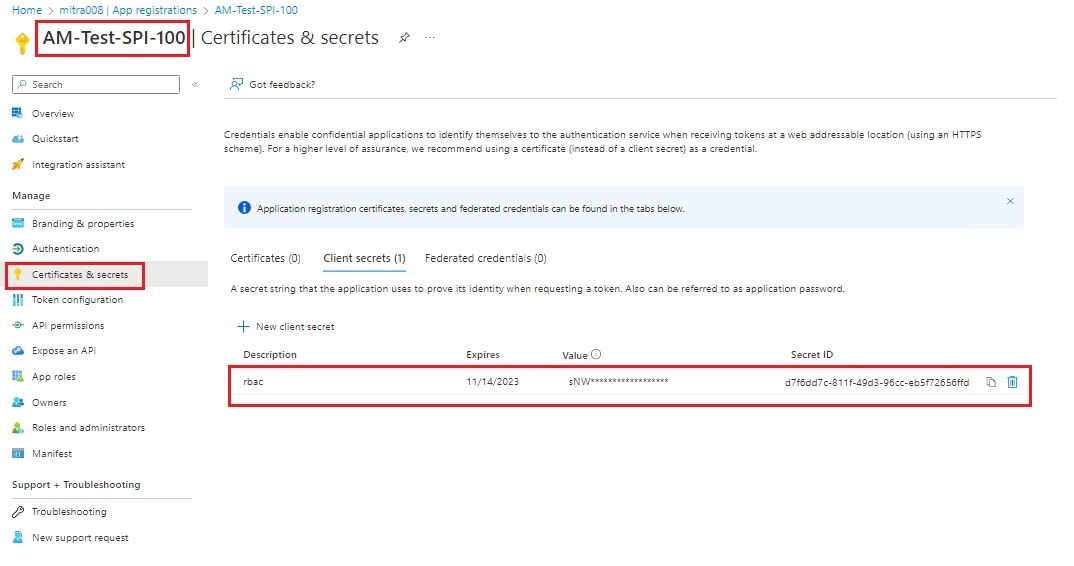
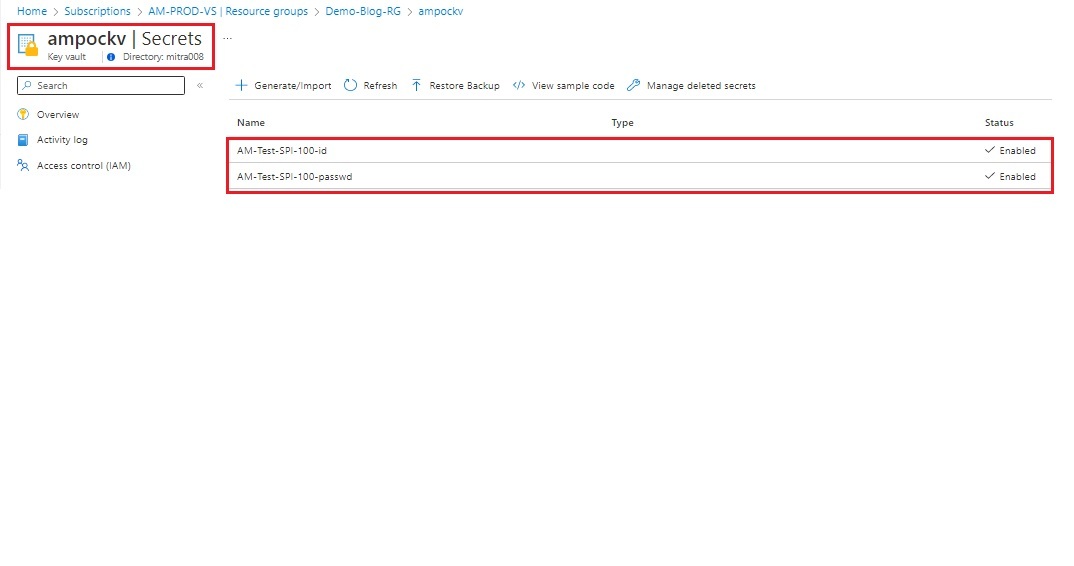
| Store the Service Principal Application ID and Secret in Key Vault. |
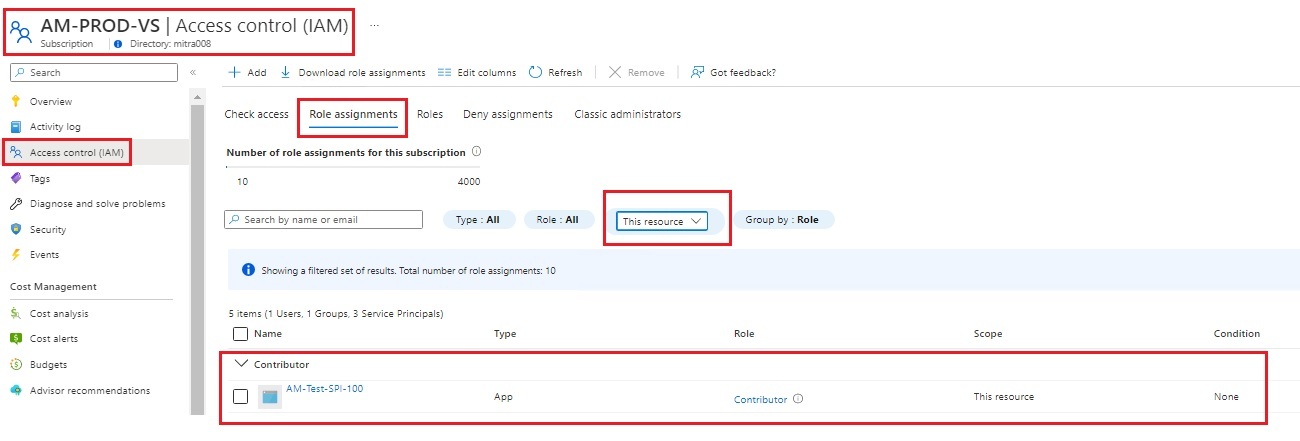
| Assign the Service Principal, "Contributor" RBAC (Role Based Access Control) on Subscription Level. |
| Set Service Principal Secret as an Environmental Variable for creating Azure DevOps Service Connection. |
| Set PAT (Personal Access Token) as an environment variable for DevOps Login. |
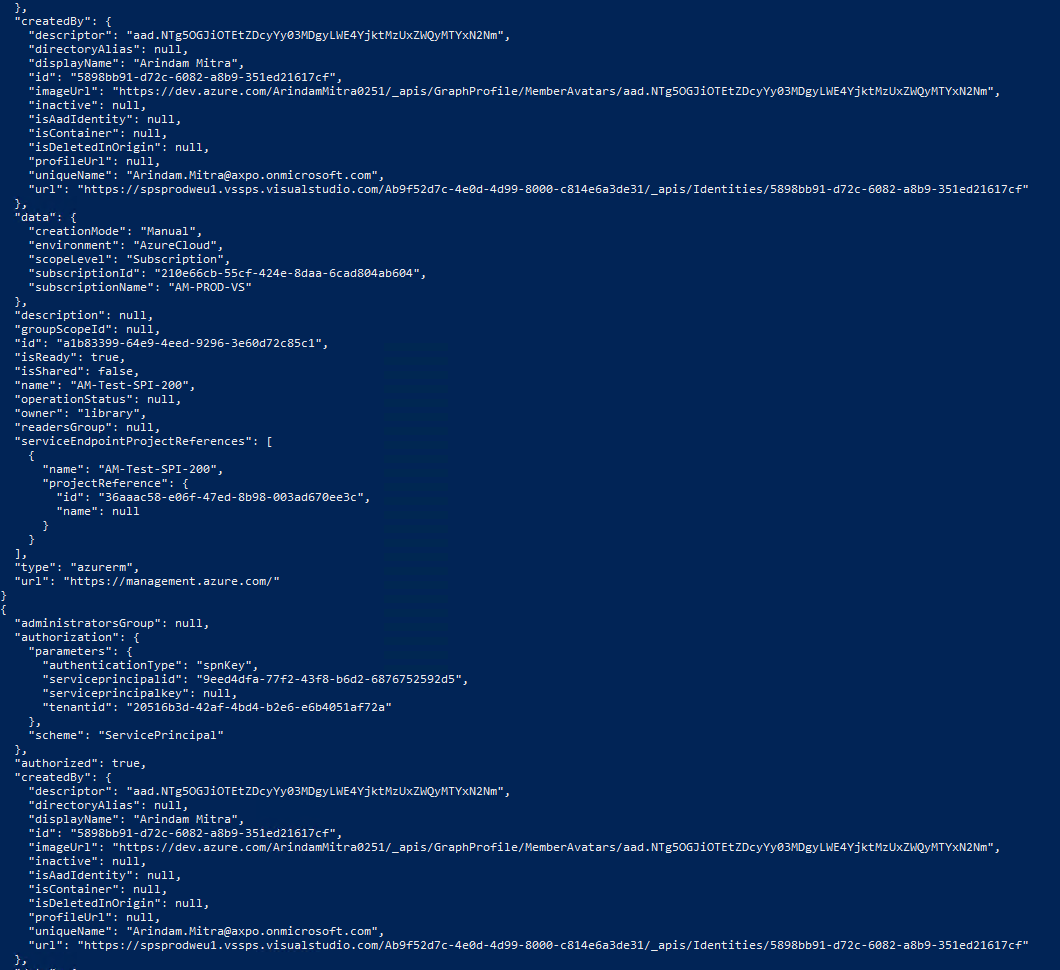
| Create Azure DevOps Service Connection. |
| Grant Access to all Pipelines to the Newly Created Azure DevOps Service Connection. |
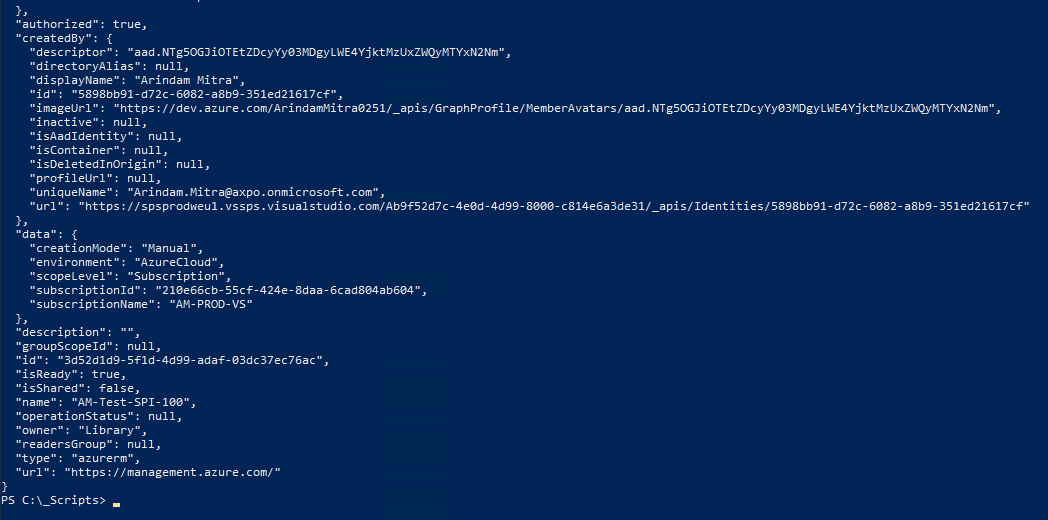
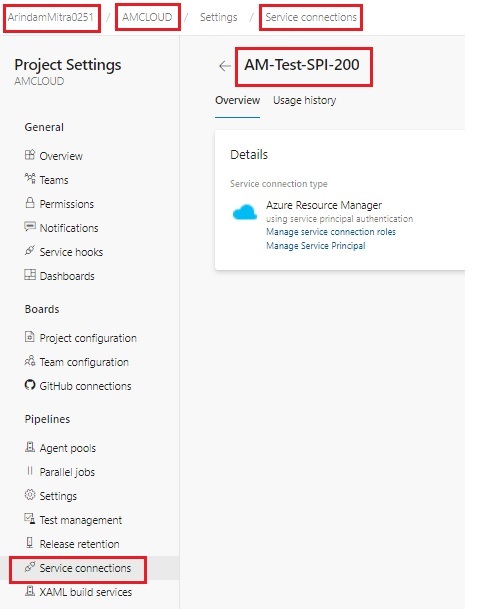
| Verify Service Connection. |
| REQUIREMENTS:- |
|---|
- Azure Subscription.
- Azure DevOps Organisation and Project.
- Full Access PAT (Personal Access Token).
- The Identity executing the script has required privilege to a) Create Service Principal in Azure Active Directory, b) Assign RBAC, and c) Create Secret in Key vault.
| CODE REPOSITORY:- |
|---|
| {% github arindam0310018/15-Nov-2022-DevOpsCLI__Create-Service-Connection %} |
| BELOW FOLLOWS THE CODE SNIPPET:- |
|---|
| USE CASE #1:- |
|---|
| CREATE AZURE DEVOPS SERVICE CONNECTION WITH PAT AS USER INPUT (Create-DevOps-Service-Connection-Prompt-PAT.ps1):- |
|---|
##############
# VARIABLES:-
##############
$spiname = "AM-Test-SPI-100"
$rbac = "Contributor"
$devopsOrg = "https://dev.azure.com/arindammitra0251/"
$devopsPrj = "AMCLOUD"
$subsID = "210e66cb-55cf-424e-8daa-6cad804ab604"
$subsName = "AM-PROD-VS"
$tenantID = "20516b3d-42af-4bd4-b2e6-e6b4051af72a"
$kv = "ampockv"
##############
# CORE SCRIPT:-
##############
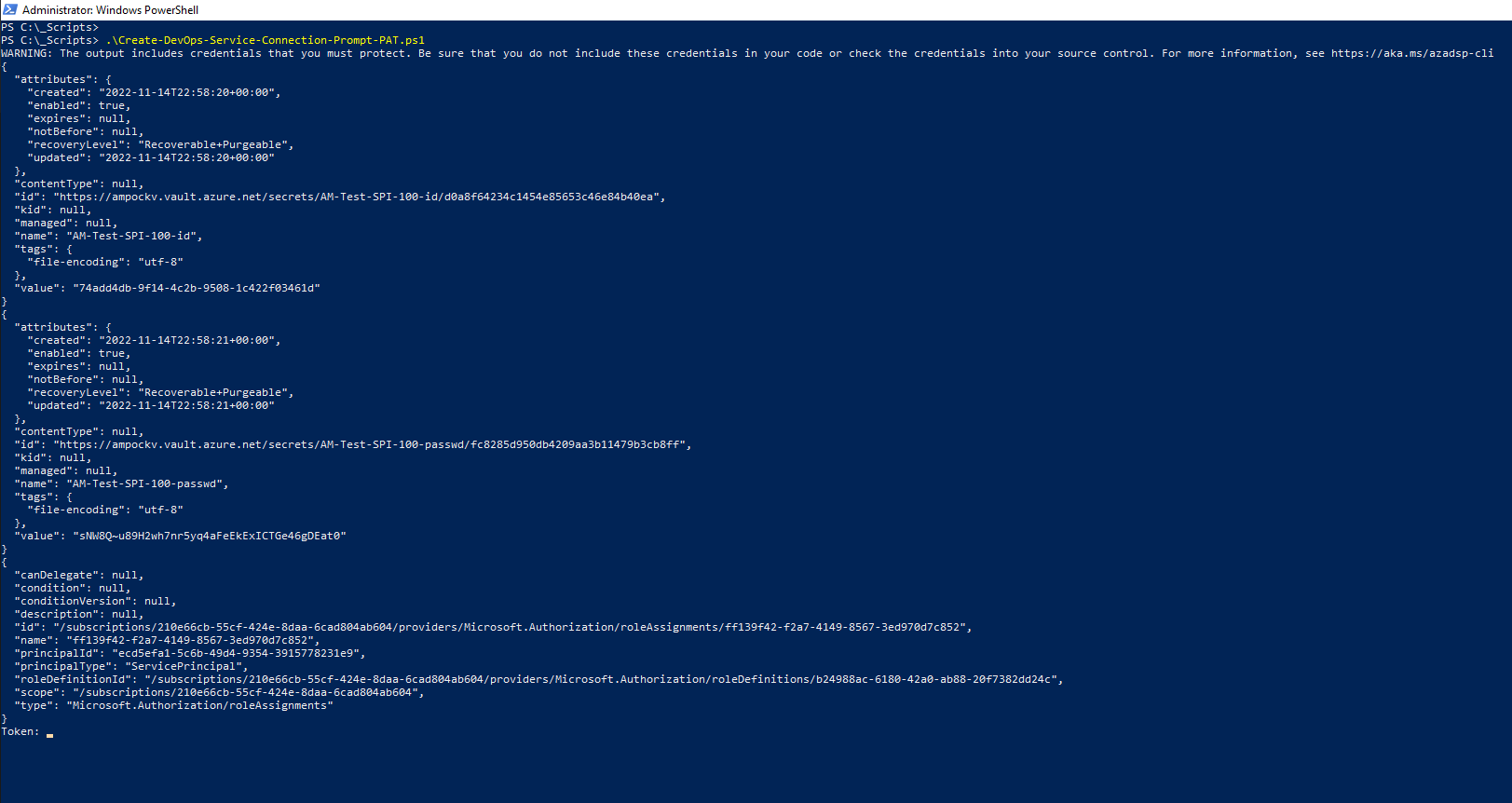
# Create Service Principal and Store Secret in a variable:-
$spipasswd = az ad sp create-for-rbac -n $spiname --query "password" -o tsv
# Query the Application ID of the Service Principal and Store it in a variable:-
$spiID = az ad sp list --display-name $spiname --query [].appId -o tsv
# Store the Service Principal Application ID and Secret in Key Vault:-
az keyvault secret set --name $spiname-id --vault-name $kv --value $spiID
az keyvault secret set --name $spiname-passwd --vault-name $kv --value $spipasswd
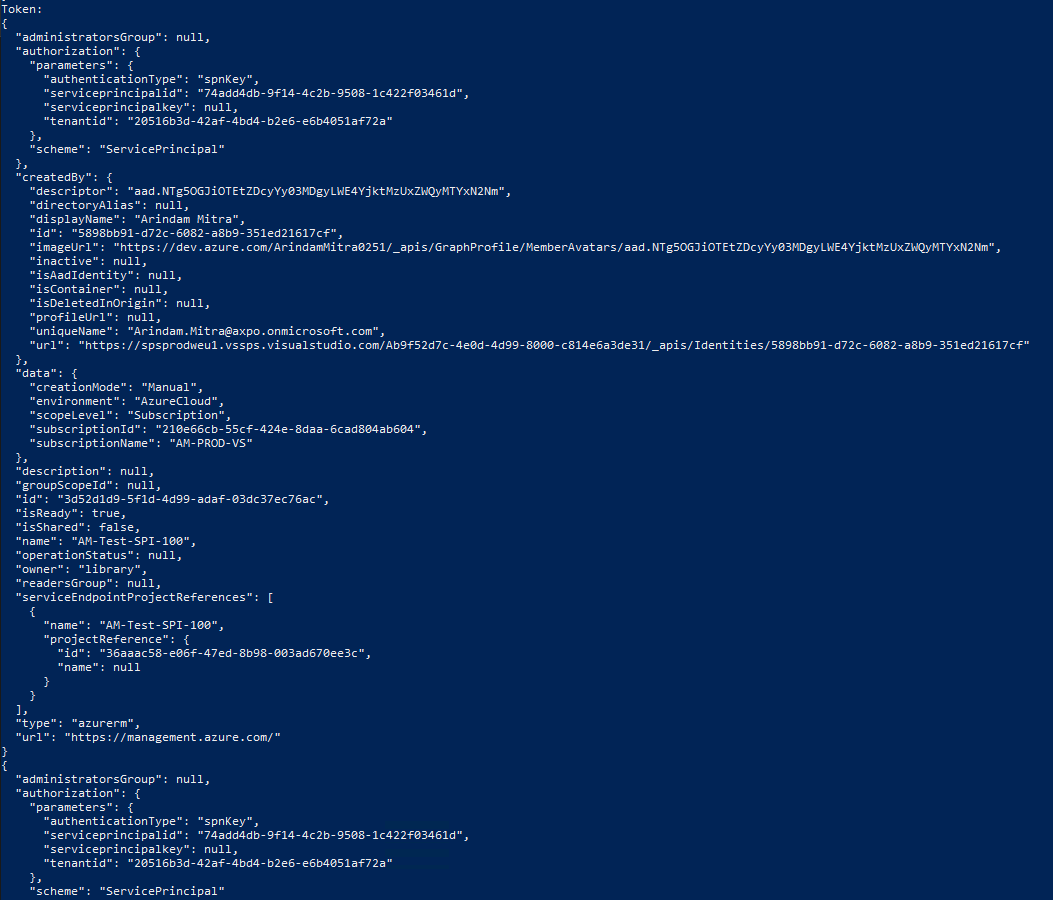
# Assign the Service Principal, "Contributor" RBAC on Subscription Level:-
az role assignment create --assignee "$spiID" --role "$rbac" --scope "/subscriptions/$subsID"
#Set Service Principal Secret as an Environment Variable for creating Azure DevOps Service Connection:-
$env:AZURE_DEVOPS_EXT_AZURE_RM_SERVICE_PRINCIPAL_KEY=$spipasswd
# Perform DevOps Login. It will Prompt for PAT:-
az devops login
# Set Default DevOps Organisation and Project:-
az devops configure --defaults organization=$devopsOrg project=$devopsPrj
# Create DevOps Service Connection:-
az devops service-endpoint azurerm create --azure-rm-service-principal-id $spiID --azure-rm-subscription-id $subsID --azure-rm-subscription-name $subsName --azure-rm-tenant-id $tenantID --name $spiname --org $devopsOrg --project $devopsPrj
# Grant Access to all Pipelines to the Newly Created DevOps Service Connection:-
$srvEndpointID = az devops service-endpoint list --query "[?name=='$spiname'].id" -o tsv
az devops service-endpoint update --id $srvEndpointID --enable-for-all
| USE CASE #2:- |
|---|
| CREATE AZURE DEVOPS SERVICE CONNECTION WITH PAT AS ENVIRONMENT VARIABLE (Create-DevOps-Service-Connection-Without-Prompting-PAT.ps1):- |
|---|
##############
# VARIABLES:-
##############
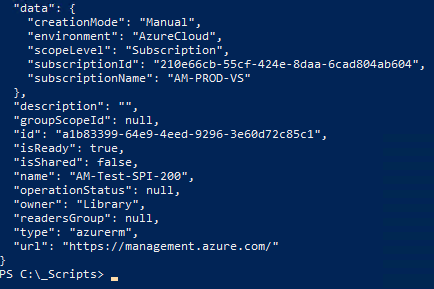
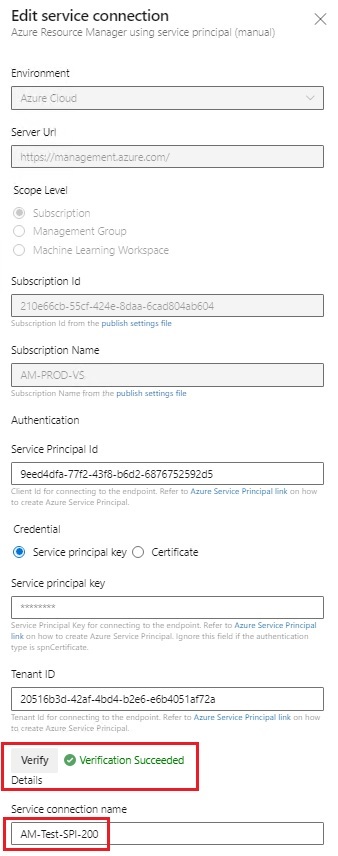
$spiname = "AM-Test-SPI-200"
$rbac = "Contributor"
$pat = "<Provide your own PAT>"
$devopsOrg = "https://dev.azure.com/arindammitra0251/"
$devopsPrj = "AMCLOUD"
$subsID = "210e66cb-55cf-424e-8daa-6cad804ab604"
$subsName = "AM-PROD-VS"
$tenantID = "20516b3d-42af-4bd4-b2e6-e6b4051af72a"
$kv = "ampockv"
##############
# CORE SCRIPT:-
##############
# Create Service Principal and Store Secret in a variable:-
$spipasswd = az ad sp create-for-rbac -n $spiname --query "password" -o tsv
# Query the Application ID of the Service Principal and Store it in a variable:-
$spiID = az ad sp list --display-name $spiname --query [].appId -o tsv
# Store the Service Principal Application ID and Secret in Key Vault:-
az keyvault secret set --name $spiname-id --vault-name $kv --value $spiID
az keyvault secret set --name $spiname-passwd --vault-name $kv --value $spipasswd
# Assign the Service Principal, "Contributor" RBAC on Subscription Level:-
az role assignment create --assignee "$spiID" --role "$rbac" --scope "/subscriptions/$subsID"
#Set Service Principal Secret as an Environment Variable for creating Azure DevOps Service Connection:-
$env:AZURE_DEVOPS_EXT_AZURE_RM_SERVICE_PRINCIPAL_KEY=$spipasswd
# Set PAT as an environment variable for DevOps Login:-
$env:AZURE_DEVOPS_EXT_PAT = $pat
# Set Default DevOps Organisation and Project:-
az devops configure --defaults organization=$devopsOrg project=$devopsPrj
# Create DevOps Service Connection:-
az devops service-endpoint azurerm create --azure-rm-service-principal-id $spiID --azure-rm-subscription-id $subsID --azure-rm-subscription-name $subsName --azure-rm-tenant-id $tenantID --name $spiname --org $devopsOrg --project $devopsPrj
# Grant Access to all Pipelines to the Newly Created DevOps Service Connection:-
$srvEndpointID = az devops service-endpoint list --query "[?name=='$spiname'].id" -o tsv
az devops service-endpoint update --id $srvEndpointID --enable-for-all
| DIFFERENCE BETWEEN BOTH USE CASES:- |
|---|
| In Use Case 1, PAT is prompted as User Input during script execution. |
| In Use Case 2, PAT is set as Environment variable so that it is not prompted as User Input during script execution. |
Now, let me explain the script, part by part for better understanding.
| VARIABLES:- |
|---|
USE CASE 1:-
##############
# VARIABLES:-
##############
$spiname = "AM-Test-SPI-100"
$rbac = "Contributor"
$devopsOrg = "https://dev.azure.com/arindammitra0251/"
$devopsPrj = "AMCLOUD"
$subsID = "210e66cb-55cf-424e-8daa-6cad804ab604"
$subsName = "AM-PROD-VS"
$tenantID = "20516b3d-42af-4bd4-b2e6-e6b4051af72a"
$kv = "ampockv"
USE CASE 2:-
##############
# VARIABLES:-
##############
$spiname = "AM-Test-SPI-200"
$rbac = "Contributor"
$pat = "<Provide your own PAT>"
$devopsOrg = "https://dev.azure.com/arindammitra0251/"
$devopsPrj = "AMCLOUD"
$subsID = "210e66cb-55cf-424e-8daa-6cad804ab604"
$subsName = "AM-PROD-VS"
$tenantID = "20516b3d-42af-4bd4-b2e6-e6b4051af72a"
$kv = "ampockv"
| NOTE:- |
|---|
| Please change the values of the variables accordingly. |
| The entire script is build using Variables. No Values are Hardcoded. Changing the values of the variables should help you execute the script seamlessly. |
| CORE SCRIPT:- |
|---|
Create Service Principal and Store Secret in a variable:-
$spipasswd = az ad sp create-for-rbac -n $spiname --query "password" -o tsv
Query the Application ID of the Service Principal and Store it in a variable:-
$spiID = az ad sp list --display-name $spiname --query [].appId -o tsv
Store the Service Principal Application ID and Secret in Key Vault:-
az keyvault secret set --name $spiname-id --vault-name $kv --value $spiID
az keyvault secret set --name $spiname-passwd --vault-name $kv --value $spipasswd
Assign the Service Principal, "Contributor" RBAC on Subscription Level:-
az role assignment create --assignee "$spiID" --role "$rbac" --scope "/subscriptions/$subsID"
Set Service Principal Secret as an Environment Variable for creating Azure DevOps Service Connection:-
$env:AZURE_DEVOPS_EXT_AZURE_RM_SERVICE_PRINCIPAL_KEY=$spipasswd
Perform DevOps Login. It will Prompt for PAT Token:-
az devops login
OR
Set PAT as an environment variable for DevOps Login:-
$env:AZURE_DEVOPS_EXT_PAT = $pat
Set Default DevOps Organisation and Project:-
az devops configure --defaults organization=$devopsOrg project=$devopsPrj
Create DevOps Service Connection:-
az devops service-endpoint azurerm create --azure-rm-service-principal-id $spiID --azure-rm-subscription-id $subsID --azure-rm-subscription-name $subsName --azure-rm-tenant-id $tenantID --name $spiname --org $devopsOrg --project $devopsPrj
Grant Access to all Pipelines to the Newly Created DevOps Service Connection:-
$srvEndpointID = az devops service-endpoint list --query "[?name=='$spiname'].id" -o tsv
az devops service-endpoint update --id $srvEndpointID --enable-for-all
NOW ITS TIME TO TEST
| TEST CASES:- |
|---|
Hope You Enjoyed the Session!!!
Stay Safe | Keep Learning | Spread Knowledge